Security News

Organizations are ramping up their use of encrypted traffic to lock down data. Could they be making it easier to hide threats in the process? On one hand, encryption means enhanced privacy, but it can also make the job of security analysts much harder.

BLACK HAT ASIA Researchers at US/Israeli infosec outfit SafeBreach last Friday discussed flaws in Microsoft and Kaspersky security products that can potentially allow the remote deletion of files. Speaking at the Black Hat Asia conference in Singapore, SafeBreach's VP of Security Research Tomer Bar and security researcher Shmuel Cohen explained that Microsoft Defender and Kaspersky's Endpoint Detection and Response can be made to detect false positive indicators of malicious files - and then to delete them.

Microsoft has patched today a Windows Defender SmartScreen zero-day exploited in the wild by a financially motivated threat group to deploy the DarkMe remote access trojan.The hacking group was spotted using the zero-day in attacks on New Year's Eve day by Trend Micro security researchers.

Microsoft is deprecating Defender Application Guard for Edge for Business users. Microsoft Defender Application Guard blocks potential threats by opening them in a secure sandbox using hardware-based virtualization.

Microsoft is deprecating Defender Application Guard for Office and the Windows Security Isolation APIs, and it recommends Defender for Endpoint attack surface reduction rules, Protected View, and...

Microsoft has announced a new bug bounty program aimed at unearthing vulnerabilities in Defender-related products and services, and is offering participants the possibility to earn up to $20,000 for the most critical bugs. Microsoft Defender includes various products and services that are build to secure and protect Microsoft users.

Microsoft has unveiled a new bug bounty program aimed at the Microsoft Defender security platform, with rewards between $500 and $20,000.Currently, the Microsoft Defender Bounty Program is limited in scope and will focus solely on Microsoft Defender for Endpoint APIs.

Today’s security leaders must manage a constantly evolving attack surface and a dynamic threat environment due to interconnected devices, cloud services, IoT technologies, and hybrid work...

The feature aims to help organizations disrupt human-operated attacks like ransomware, business email compromise and adversary-in-the-middle, which start - more often than not - with compromised user accounts. Microsoft Defender for Endpoint is Microsoft's enterprise extended detection and response solution that detects threats on networks and systems and allows organizations' security staff to investigate and respond to attacks.
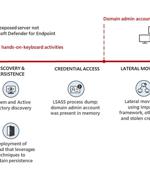
Microsoft on Wednesday said that a user containment feature in Microsoft Defender for Endpoint helped thwart a "large-scale remote encryption attempt" made by Akira ransomware actors targeting an...