Security News

Cybercriminals are increasingly leveraging legitimate HTTP client tools to facilitate account takeover (ATO) attacks on Microsoft 365 environments. Enterprise security company Proofpoint said it...

Cybersecurity researchers have revealed several malicious packages on the npm registry that have been found impersonating the Nomic Foundation's Hardhat tool in order to steal sensitive data from...

Cybercriminals are using a variety of new methods to target organizations across industries. In this article, we examine the most pressing trends and findings from the 2024 surveys on the growing...

AI changes how organizations look at cybersecurity GenAI is compromising security while promising efficiency This article highlights key findings from 2024 reports on AI and GenAI technologies,...

Breaches in 2024 had less impact on consumers’ trust in brands compared to the previous year (a 6.5% decrease from 62% in 2023 to 58% in 2024), according to a recent Vercara report. Most consumers...

Russian law enforcement has arrested and indicted notorious ransomware affiliate Mikhail Pavlovich Matveev (also known as Wazawaka, Uhodiransomwar, m1x, and Boriselcin) for developing malware and...
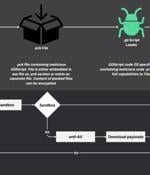
A popular open-source game engine called Godot Engine is being misused as part of a new GodLoader malware campaign, infecting over 17,000 systems since at least June 2024. "Cybercriminals have...

Threat actors are using an ingenious new way for covertly delivering malware to a wide variety of operating systems and platforms: they have created a malware loader that uses Godot Engine, an...

Ransomware gangs recruit pen testers to improve attack reliability Threat actors employ pen testers to improve ransomware effectiveness Threat actors are recruiting pen testers to test and improve...

Hijacking domains using a ‘Sitting Ducks attack’ remains an underrecognized topic in the cybersecurity community. Few threat researchers are familiar with this attack vector, and knowledge is...