Security News
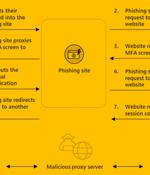
A new phishing-as-a-service toolkit dubbed EvilProxy is being advertised on the criminal underground as a means for threat actors to bypass two-factor authentication protections employed against online services. "EvilProxy actors are using reverse proxy and cookie injection methods to bypass 2FA authentication - proxifying victim's session," Resecurity researchers said in a Monday write-up.

Researchers discovered a private Telegram channel-based backdoor in the information stealing malware, dubbed Prynt Stealer, which its developer added with the intention of secretly stealing a copy of victims' exfiltrated data when used by other cybercriminals. Prynt Stealer, which came to light earlier this April, comes with capabilities to log keystrokes, steal credentials from web browsers, and siphon data from Discord and Telegram.

New research indicates that over 80,000 Hikvision surveillance cameras in the world today are vulnerable to an 11 month-old command injection flaw. Hikvision - short for Hangzhou Hikvision Digital Technology - is a Chinese state-owned manufacturer of video surveillance equipment.

Imperva releases data showing that 25% of all gambling sites were hit with DDoS attacks executed by botnets in June. As the Wimbledon tennis tournament began at the end of June, DDoS attacks increased and impacted 10% of gambling sites.

In a sign that malicious actors continue to find ways to work around Google Play Store security protections, researchers have spotted a previously undocumented Android dropper trojan that's currently in development. Dubbed BugDrop by the Dutch security firm, the dropper app is explicitly designed to defeat new features introduced in the upcoming version of Android that aim to make it difficult for malware to request Accessibility Services privileges from victims.

Cybercriminals are tapping the built-in services of popular messaging apps like Telegram and Discord as ready-made platforms to help them perform their nefarious activity in persistent campaigns that threaten users, researchers have found. Threat actors are tapping the multi-feature nature of messaging apps-in particularly their content-creation and program-sharing components-as a foundation for info-stealing, according to new research from Intel 471.

Resecurity, a Los Angeles-based cybersecurity company protecting Fortune 500 companies worldwide, has registered an increase in malicious activity targeting law enforcement agencies at the beginning of Q2 2022. This Help Net Security video highlights how cyber attacks affect law enforcement agencies worldwide.

Why North Korean cybercriminals are targeting businesses with ransomware. What happens when a hostile nation-state sponsors that same tactic? A new report by the Microsoft Threat Intelligence Center examines a series of ransomware attacks with ties to North Korea.

The choice of Tampa for his trial was because a known victim of one of his "NetWalker" ransomware attacks is based there. The NetWalker Ransomware was a specific type of malicious software that was used to compromise and restrict access to a victim's computer network in an effort to extort a ransom.

Resecurity, Inc. has identified a spike in phishing content delivered via Azure Front Door, a cloud CDN service provided by Microsoft. According to experts, such tactics confirm how the bad actors are continuously looking to enhance their tactics and procedures to avoid phishing detection using world-known cloud services.