Security News

The Europol report also reported on cybercriminals' use of cryptocurrencies and how their techniques are more sophisticated. The Europol report reported on cybercriminals' use of cryptocurrencies and how their techniques are more sophisticated.

Discover stories about threat actors' latest tactics, techniques, and procedures from Cybersixgill's threat experts each month. Each story brings you details on emerging underground threats, the threat actors involved, and how you can take action to mitigate risks.
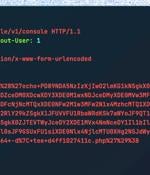
Threat actors are actively exploiting a recently disclosed critical security flaw in the WooCommerce Payments WordPress plugin as part of a massive targeted campaign. "Large-scale attacks against the vulnerability, assigned CVE-2023-28121, began on Thursday, July 14, 2023 and continued over the weekend, peaking at 1.3 million attacks against 157,000 sites on Saturday, July 16, 2023," Wordfence security researcher Ram Gall said in a Monday post.
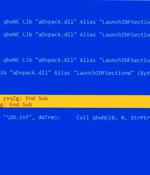
Microsoft Word documents exploiting known remote code execution flaws are being used as phishing lures to drop malware called LokiBot on compromised systems. The Word file that weaponizes CVE-2021-40444 contains an external GoFile link embedded within an XML file that leads to the download of an HTML file, which exploits Follina to download a next-stage payload, an injector module written in Visual Basic that decrypts and launches LokiBot.
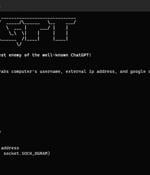
According to findings from SlashNext, a new generative AI cybercrime tool called WormGPT has been advertised on underground forums as a way for adversaries to launch sophisticated phishing and business email compromise attacks.In the hands of a bad actor, tools like WormGPT could be a powerful weapon, especially as OpenAI ChatGPT and Google Bard are increasingly taking steps to combat the abuse of large language models to fabricate convincing phishing emails and generate malicious code.

Computer scientists at the University of Waterloo have discovered a method of attack that can successfully bypass voice authentication security systems with up to a 99% success rate after only six tries. Voice authentication - which allows companies to verify the identity of their clients via a supposedly unique "Voiceprint" - has increasingly been used in remote banking, call centers and other security-critical scenarios.
An active financially motivated campaign is targeting vulnerable SSH servers to covertly ensnare them into a proxy network. "This is an active campaign in which the attacker leverages SSH for remote access, running malicious scripts that stealthily enlist victim servers into a peer-to-peer proxy network, such as Peer2Profit or Honeygain," Akamai researcher Allen West said in a Thursday report.

As COVID-19 medical and economic programs began to wind down, attackers had to find new ways to make a living by honing their social engineering skills, commoditising once-sophisticated attack techniques, and creatively searching for new opportunities in unexpected places. From scaling brute-force and targeted attacks on cloud tenants to the surge in conversational smishing attacks and proliferation of multifactor authentication bypass, the cyber-attack landscape witnessed significant developments on several fronts in 2022.

In this Help Net Security video, Jim Simpson, Director of Threat Intelligence at Searchlight Cyber, discusses how cybercriminals employ specialized strategies when targeting energy companies. This is primarily due to the sensitive and valuable information these organizations hold and their critical role in infrastructure, making them particularly attractive for economic and geopolitical disruption.
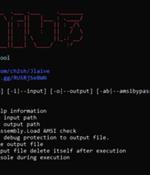
A fully undetectable malware obfuscation engine named BatCloak is being used to deploy various malware strains since September 2022, while persistently evading antivirus detection. The samples grant "Threat actors the ability to load numerous malware families and exploits with ease through highly obfuscated batch files," Trend Micro researchers said.