Security News
A new set of malicious packages has been unearthed in the Python Package Index (PyPI) repository that masqueraded as cryptocurrency wallet recovery and management services, only to siphon...

The threat actors behind the Rhadamanthys information stealer have added new advanced features to the malware, including using artificial intelligence (AI) for optical character recognition (OCR)...

Plus: SpaceX plans Vietnam investment; Yahoo! Japan content moderation secrets; LG offloads Chinese display factory; and more ASIA IN BRIEF It's not often The Register writes about a...
Cybersecurity researchers have discovered a malicious Android app on the Google Play Store that enabled the threat actors behind it to steal approximately $70,000 in cryptocurrency from victims...

The U.S. government on Thursday sanctioned two cryptocurrency exchanges and unsealed an indictment against a Russian national for his alleged involvement in the operation of several money...

The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) has sanctioned PM2BTC and Cryptex, two cryptocurrency exchanges that laundered funds from Russian ransomware gangs and other...

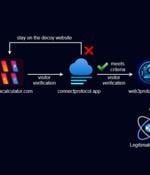
A crypto draining app mimicking the legitimate 'WalletConnect' project has been distributed over Google Play for five months getting more than 10,000 downloads. [...]

A massive infostealer malware operation encompassing thirty campaigns targeting a broad spectrum of demographics and system platforms has been uncovered, attributed to a cybercriminal group named...

Just one victim milked of nearly a quarter of a billion bucks Two individuals are in cuffs and facing serious charges in connection to a major theft of cryptocurrency worth more than $230 million...

German law enforcement seized 47 cryptocurrency exchange services hosted in the country that facilitated illegal money laundering activities for cybercriminals, including ransomware gangs. [...]