Security News
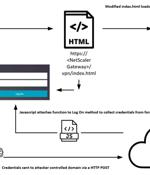
A recently disclosed critical flaw in Citrix NetScaler ADC and Gateway devices is being exploited by threat actors to conduct a credential harvesting campaign. IBM X-Force, which uncovered the...

Hackers are conducting a large-scale campaign to exploit the recent CVE-2023-3519 flaw in Citrix NetScaler Gateways to steal user credentials. The flaw is a critical unauthenticated remote code execution bug discovered as a zero-day in July that impacts Citrix NetScaler ADC and NetScaler Gateway.

23andMe has confirmed to BleepingComputer that it is aware of user data from its platform circulating on hacker forums and attributes the leak to a credential-stuffing attack. Recently, a threat actor leaked samples of data that was allegedly stolen from a genetics firm and, a few days later, offered to sell data packs belonging to 23andMe customers.

Cisco released security updates to fix a Cisco Emergency Responder vulnerability that let attackers log into unpatched systems using hard-coded credentials. "This vulnerability is due to the presence of static user credentials for the root account that are typically reserved for use during development," Cisco explained in an advisory issued today.

Weak password policies leave organizations vulnerable to attacks. But are the standard password complexity requirements enough to secure them? 83% of compromised passwords would satisfy the...

Json from CRED FILE NAMES file name array to GCLOUD CREDS FILES file name array[+] added netrc, kubeconfig, adc. Db from CRED FILE NAMES file name array[-] removed dload function[+] added commented dload function invocation for posting final results[+] added commented wget command to download and execute https://everlost.
A new "Mass-spreading" social engineering campaign is targeting users of the Zimbra Collaboration email server with an aim to collect their login credentials for use in follow-on operations. "Initially, the target receives an email with a phishing page in the attached HTML file," ESET researcher Viktor Šperka said in a report.

At a little overt halfway through 2023, credential theft is still a major thorn in the side of IT teams. The 2023 Verizon Data Breach Investigations Report revealed that 83% of breaches involved external actors, with almost all attacks being financially motivated.

Is your organization constantly under threat from credential phishing? Even with comprehensive security awareness training, many employees still fall victim to credential phishing scams. What if you could outsmart these criminals and protect your organization?

Read about a new tool advertised on the Dark Web called WormGPT. As artificial intelligence technology such as ChatGPT continues to improve, so does its potential for misuse by cybercriminals. ChatGPT credentials and jailbreak prompts on the Dark Web ChatGPT stolen credentials on the Dark Web.