Security News

A new phishing kit has been released that allows red teamers and cybercriminals to create progressive web Apps that display convincing corporate login forms to steal credentials. D0x demonstrates how to create PWA apps to display corporate login forms, even with a fake address bar showing the normal corporate login URL to make it look more convincing.

A new trove of 361 million email addresses has been added to Have I Been Pwned?, the free online service through which users can check whether their account credentials and other data has been compromised in one or more data breaches. The data includes lists of credentials for accounts grouped either by service or country.

Cloud computing and analytics company Snowflake said a "limited number" of its customers have been singled out as part of a targeted campaign. "We have not identified evidence suggesting this...

Have attackers compromised Snowflake or just their customers' accounts and databases? Conflicting claims muddy the situation. "From an enterprise perspective, Snowflake is typically set up as a cloud-based data warehousing solution. Enterprises choose a cloud provider, and set up their Snowflake account within the chosen region. Data is ingested from various sources, transformed, and analyzed using SQL," Doron Karmi, Senior Cloud Security Researcher at Mitiga, told Help Net Security.
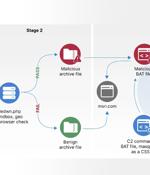
The Russian GRU-backed threat actor APT28 has been attributed as behind a series of campaigns targeting networks across Europe with the HeadLace malware and credential-harvesting web pages. APT28,...

Okta is warning that a cross-origin authentication feature in Customer Identity Cloud (CIC) is susceptible to credential stuffing attacks orchestrated by threat actors. "We observed that the...

Okta warns that a Customer Identity Cloud feature is being targeted in credential stuffing attacks, stating that numerous customers have been targeted since April. Okta says it identified credential stuffing attacks starting on April 15, 2024, which targeted endpoints utilizing Customer Identity Cloud's cross-origin authentication feature.

Malicious Android apps masquerading as Google, Instagram, Snapchat, WhatsApp, and X (formerly Twitter) have been observed to steal users' credentials from compromised devices. "This malware uses...

There is growing consensus on how to address the challenge of deepfakes in media and businesses, generated through technologies such as AI. Earlier this year, Google announced that it was joining the Coalition for Content Provenance and Authenticity as a steering committee member - other organisations in the C2PA include OpenAI, Adobe, Microsoft, AWS and the RIAA. With growing concern about AI misinformation and deepfakes, IT professionals will want to pay close attention to the work of this body, and particularly Content Credentials, as the industry formalises standards governing how visual and video data is managed. Content Credentials are a form of digital metadata that creators can attach to their content to ensure proper recognition and promote transparency.
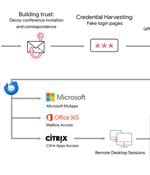
The Iranian state-backed hacking outfit called APT42 is making use of enhanced social engineering schemes to infiltrate target networks and cloud environments. Targets of the attack...