Security News

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

The Cyber Police of Ukraine has announced the arrest of a local man who is suspected to have offered their services to LockBit and Conti ransomware groups. The unnamed 28-year-old native of the...

The Ukraine cyber police have arrested a 28-year-old Russian man in Kyiv for working with Conti and LockBit ransomware operations to make their malware undetectable by antivirus software and conducting at least one attack himself. The Ukrainian police reported that the arrested individual was a specialist in developing custom crypters for packing the ransomware payloads into what appeared as safe files, making them FUD to evade detection by the popular antivirus products.

Security researchers analyzing the activity of the recently emerged 3AM ransomware operation uncovered close connections with infamous groups, such as the Conti syndicate and the Royal ransomware gang. The 3AM ransomware gang's activity was first documented publicly in mid-September when the Threat Hunter Team at Symantec, now part of Broadcom, revealed that they noticed threat actors switching to ThreeAM ransomware after failing to deploy the LockBit malware.

It started as a slow ransomware news week but slowly picked up pace with the Department of Justice announcing indictments on TrickBot and Conti operations members. In other news, Cisco confirmed that ransomware gangs are exploiting a zero-day in Cisco VPN appliances after BleepingComputer's, SentinelOnes, and Rapid7's reporting on its abuse by the Akira ransomware operation.

The USA and the United Kingdom have sanctioned eleven Russian nationals associated with the TrickBot and Conti ransomware cybercrime operations. After numerous takedown attempts by the U.S. government, the Conti ransomware gang took control of the TrickBot operation and its development, using it to enhance more advanced and stealthy malware, such as BazarBackdoor and Anchor.

Ex-Conti ransomware members have teamed up with the FIN7 threat actors to distribute a new malware family named 'Domino' in attacks on corporate networks. Domino is a relatively new malware family consisting of two components, a backdoor named 'Domino Backdoor,' which in turn drops a 'Domino Loader' that injects an info-stealing malware DLL into the memory of another process.
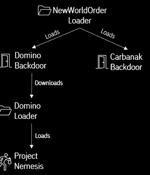
A new strain of malware developed by threat actors likely affiliated with the FIN7 cybercrime group has been put to use by the members of the now-defunct Conti ransomware gang, indicating collaboration between the two crews. The latest intrusion wave, spotted by IBM Security X-Force two months ago, involves the use of Dave Loader, a crypter previously attributed to the Conti group, to deploy the Domino backdoor.

Good news for ransomware victims: Kaspersky security researchers say they've cracked the Conti ransomware code and released a decryptor tool after uncovering leaked data belonging to the notorious Russian crime group. The security shop's analysts uncovered a newer Conti malware variant in December 2022, and the leaked keys unlock this strain of the ransomware.

A decryption tool for a modified version of the Conti ransomware could help hundreds of victims recover their files for free. The utility works with data encrypted with a strain of the ransomware that emerged after the source code for Conti was leaked last year in March [1, 2]. Hundreds of victims encrypted.