Security News

Atlassian today said miscreants have exploited a critical bug in on-premises instances of Confluence Server and Confluence Data Center to create and abuse admin accounts within the enterprise colab software. "Atlassian has been made aware of an issue reported by a handful of customers where external attackers may have exploited a previously unknown vulnerability in publicly accessible Confluence Data Center and Server instances to create unauthorized Confluence administrator accounts and access Confluence instances," according to a Wednesday advisory from the software giant.

Australian software company Atlassian released emergency security updates to fix a maximum severity zero-day vulnerability in its Confluence Data Center and Server software, which has been exploited in attacks. "Atlassian has been made aware of an issue reported by a handful of customers where external attackers may have exploited a previously unknown vulnerability in publicly accessible Confluence Data Center and Server instances to create unauthorized Confluence administrator accounts and access Confluence instances," the company said.

Atlassian has released updates to address three security flaws impacting its Confluence Server, Data Center, and Bamboo Data Center products that, if successfully exploited, could result in remote code execution on susceptible systems. CVE-2023-22505 and CVE-2023-22508 allow an "Authenticated attacker to execute arbitrary code which has high impact to confidentiality, high impact to integrity, high impact to availability, and no user interaction," the company said.
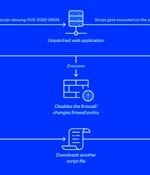
A now-patched critical security flaw affecting Atlassian Confluence Server that came to light a few months ago is being actively exploited for illicit cryptocurrency mining on unpatched installations. In one of the infection chains observed by the cybersecurity company, the flaw was leveraged to download and run a shell script on the victim's machine, which, in turn, fetched a second shell script.

A threat actor is said to have "Highly likely" exploited a security flaw in an outdated Atlassian Confluence server to deploy a never-before-seen backdoor against an unnamed organization in the research and technical services sector. "The evidence indicates that the threat actor executed malicious commands with a parent process of tomcat9.exe in Atlassian's Confluence directory," the company said.

The U.S. Cybersecurity and Infrastructure Security Agency on Friday added the recently disclosed Atlassian security flaw to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. The vulnerability, tracked as CVE-2022-26138, concerns the use of hard-coded credentials when the Questions For Confluence app is enabled in Confluence Server and Data Center instances.

CISA has added a critical Confluence vulnerability tracked as CVE-2022-26138 to its list of bugs abused in the wild, a flaw that can provide remote attackers with hardcoded credentials following successful exploitation. Today, CISA added the CVE-2022-26138 to its catalog of Known Exploited Vulnerabilities based on evidence of active exploitation.

A week after Atlassian rolled out patches to contain a critical flaw in its Questions For Confluence app for Confluence Server and Confluence Data Center, the shortcoming has now come under active exploitation in the wild.The bug in question is CVE-2022-26138, which concerns the use of a hard-coded password in the app that could be exploited by a remote, unauthenticated attacker to gain unrestricted access to all pages in Confluence.

Australian software firm Atlassian warned customers to immediately patch a critical vulnerability that provides remote attackers with hardcoded credentials to log into unpatched Confluence Server and Data Center servers. As the company revealed this week, the Questions for Confluence app creates a disabledsystemuser account with a hardcoded password to help admins migrate data from the app to the Confluence Cloud.

Atlassian has rolled out fixes to remediate a critical security vulnerability pertaining to the use of hard-coded credentials affecting the Questions For Confluence app for Confluence Server and Confluence Data Center. While this account, Atlassian says, is to help administrators migrate data from the app to Confluence Cloud, it's also created with a hard-coded password, effectively allowing viewing and editing all non-restricted pages within Confluence by default.