Security News

Microsoft Outlook can be turned into a C2 beacon to remotely execute code, as demonstrated by a new red team post-exploitation framework named "Specula," released today by cybersecurity firm TrustedSec. This C2 framework works by creating a custom Outlook Home Page using WebView by exploiting CVE-2017-11774, an Outlook security feature bypass vulnerability patched in October 2017.

Progress Software is urging users to update their Telerik Report Server instances following the discovery of a critical security flaw that could result in remote code execution. The vulnerability, tracked as CVE-2024-6327, impacts Report Server version 2024 Q2 and earlier.

Select versions of the OpenSSH secure networking suite are susceptible to a new vulnerability that can trigger remote code execution. The vulnerability, tracked as CVE-2024-6409, is distinct from CVE-2024-6387 and relates to a case of code execution in the privsep child process due to a race condition in signal handling.
Two security vulnerabilities have been disclosed in the Mailcow open-source mail server suite that could be exploited by malicious actors to achieve arbitrary code execution on susceptible...

Details have emerged about a new critical security flaw impacting PHP that could be exploited to achieve remote code execution under certain circumstances. The vulnerability, tracked as...

Ivanti on Tuesday rolled out fixes to address multiple critical security flaws in Endpoint Manager (EPM) that could be exploited to achieve remote code execution under certain circumstances. Six...
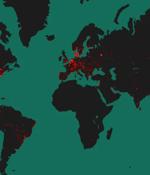
More than 50% of the 90,310 hosts have been found exposing a Tinyproxy service on the internet that's vulnerable to a critical unpatched security flaw in the HTTP/HTTPS proxy tool. The issue,...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

A new vulnerability has been discovered in the R programming language that allows arbitrary code execution upon deserializing specially crafted RDS and RDX files. [...]

The malicious code inserted into the open-source library XZ Utils, a widely used package present in major Linux distributions, is also capable of facilitating remote code execution, a new analysis...