Security News

״Defenders think in lists, attackers think in graphs,” said John Lambert from Microsoft, distilling the fundamental difference in mindset between those who defend IT systems and those who try to...
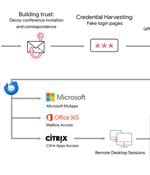
The Iranian state-backed hacking outfit called APT42 is making use of enhanced social engineering schemes to infiltrate target networks and cloud environments. Targets of the attack...

Cuttlefish, a new malware family that targets enterprise-grade small office/home office routers, is used by criminals to steal account credentials / secrets for AWS, CloudFlare, Docker, BitBucket, Alibaba Cloud and other cloud-based services. "With the stolen key material, the actor not only retrieves cloud resources associated with the targeted entity but gains a foothold into that cloud ecosystem," Black Lotus Labs researchers noted.
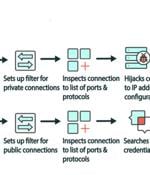
A new malware called Cuttlefish is targeting small office and home office (SOHO) routers with the goal of stealthily monitoring all traffic through the devices and gather authentication data from...

Patch network security isn't applicable in the same way for cloud environments, and few cloud providers assign Common Vulnerabilities and Exposures identifiers to vulnerabilities. For vulnerability management teams who talk exclusively in this CVE-based construct, the lack of CVEs in cloud services is a significant challenge.

In this Help Net Security video, David Kellerman, Field CTO at Cymulate, discusses how cloud security still seems to lag even as the cloud grows in popularity and usage. Many leaders are unaware that they need to secure the cloud the same way they would on-prem infrastructure and that the responsibility falls to them, not cloud providers, to do the work.

Demonstrating a sound understanding of cloud security key principles and practices opens various professional opportunities. But first, you need the right mix of technical and soft skills to...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
In this article, we'll identify some first steps you can take to establish your cloud security strategy. We'll do so by discussing the cloud security impact of individual, concrete actions featured within the CIS Critical Security Controls and the CIS Benchmarks.

Cloud Console Cartographer is an open-source tool that maps noisy log activity into highly consolidated, succinct events to help security practitioners cut through the noise and understand console behavior in their environment. "Infrastructure as code has replaced a lot of the need for console access for many organizations, but there are still plenty of instances where the console is still being used, and in some cases, you need to use the AWS console to perform certain actions. Cloud Console Cartographer cuts through the noise generated in logs by those console sessions," Daniel Bohannon, Permiso's Principal Threat Researcher, told Help Net Security.