Security News

As big tech companies from the West swiftly and happily comply with new rules that prohibit interactions with Russia, Chinese companies will soon feel pressure to do likewise - and counter-pressure to resist such calls. In early February, Russia and China re-affirmed their relationship as having "No limits" and essentially declared they are best friends forever.

The Daxin malware is taking aim at hardened government networks around the world, according to researchers, with the goal of cyberespionage. "Daxin malware is a highly sophisticated rootkit backdoor with complex, stealthy command-and-control functionality that enabled remote actors to communicate with secured devices not connected directly to the internet," warned CISA, in a Monday alert.

Security researchers have discovered Daxin, a China-linked stealthy backdoor specifically designed for deployment in hardened corporate networks that feature advanced threat detection capabilities. According to a technical report published by Symantec's Threat Hunter team today, Daxin is one of the most advanced backdoors ever seen deployed by Chinese actors.
Researchers from China's Pangu Lab have disclosed details of a "Top-tier" backdoor put to use by the Equation Group, an advanced persistent threat with alleged ties to the cyber-warfare intelligence-gathering unit of the U.S. National Security Agency. Equation Group's malware toolset became public knowledge in 2016 when a group calling itself the Shadow Brokers leaked the entire tranche of exploits used by the elite hacking team, with Kaspersky uncovering code-level similarities between the stolen files and that of samples identified as used by the threat actor.

The United States' National Security Division will wind up its "China Initiative" - an effort to combat what then-attorney general Jeff Sessions described in 2018 as "Systematic and calculated threats" posed by Beijing-backed economic espionage. "We have heard concerns from the civil rights community that the 'China Initiative' fueled a narrative of intolerance and bias," Olsen stated in a speech delivered at the National Security Institute and George Mason University.
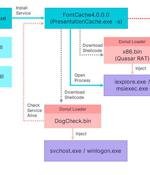
An advanced persistent threat group operating with objectives aligned with the Chinese government has been linked to an organized supply chain attack on Taiwan's financial sector. The second wave of attacks hit a peak between February 10 and 13, 2022, according to a new report published by Taiwanese cybersecurity firm CyCraft, which said the wide-ranging supply chain compromise specifically targeted the software systems of financial institutions, resulting in "Abnormal cases of placing orders."

The number of Chinese-flagged vessels in the south Pacific has surged 13-fold from 54 active vessels in 2009 to 707 in 2020, according to the SPRFMO. Meanwhile, the size of China's squid catch has grown from 70,000 tons in 2009 to 358,000. As usual, you can also use this squid post to talk about the security stories in the news that I haven't covered.

Cybersecurity researchers have detailed the inner workings of ShadowPad, a sophisticated and modular backdoor that has been adopted by a growing number of Chinese threat groups in recent years, while also linking it to the country's civilian and military intelligence agencies. ShadowPad is a modular malware platform sharing noticeable overlaps to the PlugX malware and which has been put to use in high-profile attacks against NetSarang, CCleaner, and ASUS, causing the operators to shift tactics and update their defensive measures.

The United States Federal Communications Commission has revealed that carriers have applied for $5.6 billion in funding to rip and replace China-made communications kit. The applications were made under the Secure And Trusted Communications Reimbursement Program, which offers to reimburse carriers with under ten million subscribers to ditch kit from Chinese manufacturers Huawei and ZTE. The FCC and Congress want them to do so because the USA fears made-in-China comms kit contains backdoors that Beijing could exploit to either eavesdrop on communications or cut them off entirely.

A Chinese advanced persistent threat group has been targeting Taiwanese financial institutions as part of a "Persistent campaign" that lasted for at least 18 months. The intrusions, whose primary intent was espionage, resulted in the deployment of a backdoor called xPack, granting the adversary extensive control over compromised machines, Broadcom-owned Symantec said in a report published last week.