Security News

APT41, the state-sponsored threat actor affiliated with China, breached at least six U.S. state government networks between May 2021 and February 2022 by retooling its attack vectors to take advantage of vulnerable internet-facing web applications. The exploited vulnerabilities included "a zero-day vulnerability in the USAHERDS application as well as the now infamous zero-day in Log4j," researchers from Mandiant said in a report published Tuesday, calling it a "Deliberate campaign."

Chinese hackers attempted phishing on emails affiliated with US government. According to Google's Threat Analysis Group, multiple Gmail users affiliated with the U.S. government were alerted to an attempted phishing attack by a Chinese-backed hacking group noted as APT31 in February.

The China-aligned group tracked as TA416 has been consistently targeting European diplomats since August 2020, with the most recent activity involving refreshed lures to coincide with the Russian invasion of Ukraine. According to a new report by Proofpoint, TA416 spearheads cyber-espionage operations against the EU, consistently focusing on this long-term role without reaping opportunistic gains.

Google's Threat Analysis Group has warned multiple Gmail users that they were targeted in phishing attacks conducted by a Chinese-backed hacking group tracked as APT31. "In February, we detected an APT31 phishing campaign targeting high profile Gmail users affiliated with the U.S. government," Google Threat Analysis Group's Director Shane Huntley revealed today.

Daxin is a backdoor malware that allows its controller to install further malicious software, has network tunneling capabilities, can relay communications across infected nodes, is able to hijack legitimate TCP/IP connections and is otherwise an incredibly complex piece of code. As recently as November 2021, Daxin has been involved with attacks linked to Chinese actors, generally against targets with a strategic value for China.

As big tech companies from the West swiftly and happily comply with new rules that prohibit interactions with Russia, Chinese companies will soon feel pressure to do likewise - and counter-pressure to resist such calls. In early February, Russia and China re-affirmed their relationship as having "No limits" and essentially declared they are best friends forever.

The Daxin malware is taking aim at hardened government networks around the world, according to researchers, with the goal of cyberespionage. "Daxin malware is a highly sophisticated rootkit backdoor with complex, stealthy command-and-control functionality that enabled remote actors to communicate with secured devices not connected directly to the internet," warned CISA, in a Monday alert.

Security researchers have discovered Daxin, a China-linked stealthy backdoor specifically designed for deployment in hardened corporate networks that feature advanced threat detection capabilities. According to a technical report published by Symantec's Threat Hunter team today, Daxin is one of the most advanced backdoors ever seen deployed by Chinese actors.
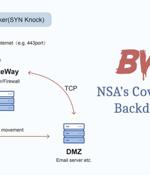
Researchers from China's Pangu Lab have disclosed details of a "Top-tier" backdoor put to use by the Equation Group, an advanced persistent threat with alleged ties to the cyber-warfare intelligence-gathering unit of the U.S. National Security Agency. Equation Group's malware toolset became public knowledge in 2016 when a group calling itself the Shadow Brokers leaked the entire tranche of exploits used by the elite hacking team, with Kaspersky uncovering code-level similarities between the stolen files and that of samples identified as used by the threat actor.

The United States' National Security Division will wind up its "China Initiative" - an effort to combat what then-attorney general Jeff Sessions described in 2018 as "Systematic and calculated threats" posed by Beijing-backed economic espionage. "We have heard concerns from the civil rights community that the 'China Initiative' fueled a narrative of intolerance and bias," Olsen stated in a speech delivered at the National Security Institute and George Mason University.