Security News

The Gallium group, believed to be a Chinese state-sponsored team, is going on the warpath with an upgraded remote access trojan that threat hunters say is difficult to detect. The backdoor, once in a compromised system, comes in three variants, each of which can communicate with the command-and-control system in one of three protocols: ICMP, HTTPS and raw TCP. All three PingPull variants have the same functionality, but each creates a custom string of code that it sends to the C2 server, which will use the unique string to identify the compromised system.

A Chinese advanced persistent threat known as Gallium has been observed using a previously undocumented remote access trojan in its espionage attacks targeting companies operating in Southeast Asia, Europe, and Africa. Called PingPull, the "Difficult-to-detect" backdoor is notable for its use of the Internet Control Message Protocol for command-and-control communications, according to new research published by Palo Alto Networks Unit 42 today.

Since 2020, Chinese state-sponsored threat actors have operated large attack campaigns exploiting publicly identified security vulnerabilities. In these campaigns, the attackers receive valid account access by exploiting Virtual Private Network vulnerabilities or other Internet-facing services without using their own distinctive or identifying malware, making it harder for threat intelligence analysts to evaluate the threat.
A technically sophisticated threat actor known as SeaFlower has been targeting Android and iOS users as part of an extensive campaign that mimics official cryptocurrency wallet websites intending to distribute backdoored apps that drain victims' funds. "As of today, the main current objective of SeaFlower is to modify Web3 wallets with backdoor code that ultimately exfiltrates the seed phrase," Confiant's Taha Karim said in a technical deep-dive of the campaign.

Threat researcher Joey Chen of Sentinel Labs says he's spotted a decade worth of cyber attacks he's happy to attribute to a single Chinese gang. Chen has named the group Aoqin Dragon, says its goal is espionage, and that it prefers targets in Australia, Cambodia, Hong Kong, Singapore, and Vietnam.

Named Aoqin Dragon, the hacking group is focused on cyber-espionage, targeting government, education, and telecommunication organizations based in Singapore, Hong Kong, Vietnam, Cambodia, and Australia. Aoqin Dragon has employed three distinct infection chains since it was first spotted, according to SentinelLabs.

A previously undocumented Chinese-speaking advanced persistent threat actor dubbed Aoqin Dragon has been linked to a string of espionage-oriented attacks aimed at government, education, and telecom entities chiefly in Southeast Asia and Australia dating as far back as 2013. This involved leveraging old and unpatched security vulnerabilities, with the decoy documents enticing targets into opening the files.
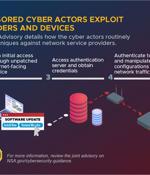
U.S. cybersecurity and intelligence agencies have warned about China-based state-sponsored cyber actors leveraging network vulnerabilities to exploit public and private sector organizations since at least 2020. The widespread intrusion campaigns aim to exploit publicly identified security flaws in network devices such as Small Office/Home Office routers and Network Attached Storage devices with the goal of gaining deeper access to victim networks.

Several US federal agencies today revealed that Chinese-backed threat actors have targeted and compromised major telecommunications companies and network service providers to steal credentials and harvest data. "Upon gaining an initial foothold into a telecommunications organization or network service provider, PRC state-sponsored cyber actors have identified critical users and infrastructure including systems critical to maintaining the security of authentication, authorization, and accounting," the advisory explains.

An "Extremely sophisticated" Chinese-speaking advanced persistent threat actor dubbed LuoYu has been observed using a malicious Windows tool called WinDealer that's delivered by means of man-on-the-side attacks. "Such attacks are especially dangerous and devastating because they do not require any interaction with the target to lead to a successful infection."