Security News

Microsoft says a Chinese cyberespionage group it tracks as Volt Typhoon has been targeting critical infrastructure organizations across the United States, including Guam, since at least mid-2021. "Microsoft assesses with moderate confidence that this Volt Typhoon campaign is pursuing development of capabilities that could disrupt critical communications infrastructure between the United States and Asia region during future crises," the Microsoft Threat Intelligence team said.

The threat actor uses a custom implant to compromise a specific TP-Link router model and steal information from it, as well as provide backdoor access to the attackers. "Horse Shell" implant found in TP-Link router firmware.

Peru in 2020 began requiring any foreign fishing boat entering its ports to use a vessel monitoring system allowing its activities to be tracked in real time 24 hours a day. The equipment, which tracks a vessel's geographic position and fishing activity through a proprietary satellite communication system, sought to provide authorities with visibility into several hundred Chinese squid vessels that every year amass off the west coast of South America.
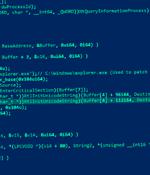
Trend Micro attributed the intrusion set to a cyber espionage group it tracks under the name Earth Longzhi, which is a subgroup within APT41 and shares overlaps with various other clusters known as Earth Baku, SparklingGoblin, and GroupCC. Earth Longzhi was first documented by the cybersecurity firm in November 2022, detailing its attacks against various organizations located in East and Southeast Asia as well as Ukraine. Attack chains mounted by the threat actor leverage vulnerable public-facing applications as entry points to deploy the BEHINDER web shell, and then leverage that access to drop additional payloads, including a new variant of a Cobalt Strike loader called CroxLoader.

The Chinese nation-state group dubbed Alloy Taurus is using a Linux variant of a backdoor called PingPull as well as a new undocumented tool codenamed Sword2033. Alloy Taurus is the constellation-themed moniker assigned to a threat actor that's known for its attacks targeting telecom companies since at least 2012.

The advanced persistent threat group referred to as Evasive Panda has been observed targeting an international non-governmental organization in Mainland China with malware delivered via update channels of legitimate applications like Tencent QQ. The attack chains are designed to distribute a Windows installer for MgBot malware, ESET security researcher Facundo Muñoz said in a new report published today. The group's hallmark is the use of the custom MgBot modular malware framework, which is capable of receiving additional components on the fly to expand on its intelligence-gathering capabilities.

Hackers are deploying new Linux malware variants in cyberespionage attacks, such as a new PingPull variant and a previously undocumented backdoor tracked as 'Sword2033. PingPull is a RAT first documented by Unit 42 last summer in espionage attacks conducted by the Chinese state-sponsored group Gallium, also known as Alloy Taurus.

Asia In Brief Chinese scientists have estimated the mass of the Milky Way. Chinese drone maker DJI whacked with $279 million patent infringement suit.

The U.S. Cybersecurity and Infrastructure Security Agency warned today of a high-severity Android vulnerability believed to have been exploited by a Chinese e-commerce app Pinduoduo as a zero-day to spy on its users. "Android Framework contains an unspecified vulnerability that allows for privilege escalation after updating an app to a higher Target SDK with no additional execution privileges needed," CISA explains.

Criminals posing as law enforcement agents of the Chinese government are shaking down Chinese nationals living the United States by accusing them of financial crimes and threatening to arrest or hurt them if they don't pay, according to the FBI. The miscreants involved in this financial fraud contact victims by spoofed phone or email messages, the bureau said in an advisory this week. Popular fake identities for the crooks include agents at the People's Republic of China Ministry of Public Security or US-based Chinese consulates.