Security News

A threat actor called Redfly has been linked to a compromise of a national grid located in an unnamed Asian country for as long as six months earlier this year using a known malware referred to as ShadowPad. "The attackers managed to steal credentials and compromise multiple computers on the organization's network," the Symantec Threat Hunter Team, part of Broadcom, said in a report shared with The Hacker News. The earliest sign of an attack targeting the Asian entity is said to have been recorded on February 23, 2023, when ShadowPad was executed on a single computer, followed by running the backdoor three months later on May 17.

The mystery of how Chinese hackers managed to steal a crucial signing key that allowed them to breach Microsoft 365's email service and access accounts of employees of 25 government agencies has been explained: they found it somewhere where it shouldn't have been - Microsoft's corporate environment. The signing key was included in the snapshot of the crashed process of a consumer signing system because of an unexpected race condition, and its presence in the crash dump wasn't detected by Microsoft's credential scanning methods.
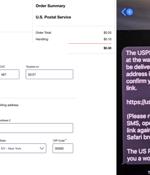
A new large-scale smishing campaign is targeting the U.S. by sending iMessages from compromised Apple iCloud accounts with an aim to conduct identity theft and financial fraud. "The Chinese-speaking threat actors behind this campaign are operating a package-tracking text scam sent via iMessage to collect personally identifying information and payment credentials from victims, in the furtherance of identity theft and credit card fraud," Resecurity said in an analysis published last week.

Nearly a third of organizations compromised by Chinese cyberspies via a critical bug in some Barracuda Email Security Gateways were government units, according to Mandiant. Mandiant continues to recommend people dump and replace their at-risk Barracuda equipment.
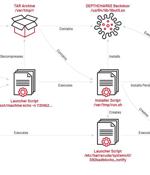
A suspected Chinese-nexus hacking group exploited a recently disclosed zero-day flaw in Barracuda Networks Email Security Gateway appliances to breach government, military, defense and aerospace, high-tech industry, and telecom sectors as part of a global espionage campaign. What's more, FOXTROT shares overlaps with an open-source rootkit called Reptile, which has been extensively used by multiple Chinese hacking crews in recent months.
China's Global Times, a state-controlled media outlet, has teased an imminent exposé of alleged US attacks on seismic data measurement stations. The statements from China are objective and professional.

A widely used Chinese language input app for Windows and Android has been found vulnerable to serious security flaws that could allow a malicious interloper to decipher the text typed by users. The findings from the University of Toronto's Citizen Lab, which carried out an analysis of the encryption mechanism used in Tencent's Sogou Input Method, an app that has over 455 million monthly active users across Windows, Android, and iOS. The vulnerabilities are rooted in EncryptWall, the service's custom encryption system, allowing network eavesdroppers to extract the textual content and access sensitive data.

A bunch of networks, including US Government networks, have been hacked by the Chinese. The hackers used forged authentication tokens to access user email, using a stolen Microsoft Azure account consumer signing key.

Two US Navy service members appeared in federal court Thursday accused of espionage and stealing sensitive military information for China in separate cases. According to Uncle Sam, Wei had been handing off photos, videos, and technical manuals about US Navy ships and systems since February 2022.

An Australian Senate Committee has recommended banning Chinese social media apps in the land down under, on grounds the Communist Party of China uses them to spread propaganda and misinformation. The Select Committee on Foreign Interference through Social Media yesterday filed its final report [PDF] which outlines the reason the committee convened: social media has become the public square in which policy debate tales place, but "Is increasingly being weaponized to spread disinformation to deliberately mislead or obscure the truth for malicious or deceptive purposes." Plenty of that disinformation comes from foreign powers, "As part of a broader, integrated strategic campaign to advance their own national interests at Australia's expense."