Security News

APT StormBamboo compromised a undisclosed internet service provider to poison DNS queries and thus deliver malware to target organizations, Volexity researchers have shared. In April 2023, ESET researchers documented the threat actor targeting an international NGO in China with malicious updates, but weren't able to pinpoint whether these updates were delivered through supply-chain compromise or adversary-in-the-middle attacks.

Japanese organizations are the target of a Chinese nation-state threat actor that leverages malware families like LODEINFO and NOOPDOOR to harvest sensitive information from compromised hosts while stealthily remaining under the radar in some cases for a time period ranging from two to three years. "The actors behind NOOPDOOR not only utilized LODEINFO during the campaign, but also utilized the new backdoor to exfiltrate data from compromised enterprise networks," it said.

The remote access trojan known as Gh0st RAT has been observed being delivered by an "Evasive dropper" called Gh0stGambit as part of a drive-by download scheme targeting Chinese-speaking Windows users. These infections stem from a fake website serving malicious installer packages masquerading as Google's Chrome browser, indicating that users searching for the software on the web are being singled out.

The Chinese hacking group tracked as 'Evasive Panda' was spotted using new versions of the Macma backdoor and the Nightdoor Windows malware. [...]

Organizations in Taiwan and a U.S. non-governmental organization based in China have been targeted by a Beijing-affiliated state-sponsored hacking group called Daggerfly using an upgraded set of malware tools. Daggerfly, also known by the names Bronze Highland and Evasive Panda, was previously observed using the MgBot modular malware framework in connection with an intelligence-gathering mission aimed at telecom service providers in Africa.
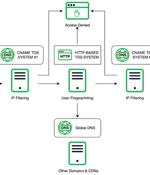
The relationship between various TDSs and DNS associated with Vigorish Viper and the final landing experience for the user A Chinese organized crime syndicate with links to money laundering and...

The China-linked advanced persistent threat group codenamed APT41 is suspected to be using an "Advanced and upgraded version" of a known malware called StealthVector to deliver a previously undocumented backdoor dubbed MoonWalk. The new variant of StealthVector - which is also referred to as DUSTPAN - has been codenamed DodgeBox by Zscaler ThreatLabz, which discovered the loader strain in April 2024.

A joint advisory from international cybersecurity agencies and law enforcement warns of the tactics used by the Chinese state-sponsored APT 40 hacking group and their hijacking of SOHO routers to launch cyberespionage attacks. Previously, APT40 was linked to a wave of attacks targeting over 250,000 Microsoft Exchange servers using the ProxyLogon vulnerabilities and campaigns involving exploiting flaws in widely used software, such as WinRAR. APT40 activity overview.

Chinese state-sponsored cyber group APT40 is amazingly fast at adapting public proof-of-concept exploits for vulnerabilities in widely used software, an advisory released by intelligence and cybersecurity agencies from eight countries warns. APT 40 "Appears to prefer exploiting vulnerable, public-facing infrastructure over techniques that require user interaction, such as phishing campaigns," and has been known to exploit vulnerabilities in software such as Log4J, Atlassian Confluence and Microsoft Exchange.

A China-nexus cyber espionage group named Velvet Ant has been observed exploiting a zero-day flaw in Cisco NX-OS Software used in its switches to deliver malware. The vulnerability, tracked as...