Security News

Intrusions allowed Beijing to 'geolocate millions of individuals, record phone calls at will' AT&T, Verizon, and Lumen Technologies confirmed that Chinese government-backed snoops accessed...

The US has never attacked Chinese critical infrastructure before, right? President-elect Donald Trump's team wants to go on the offensive against America's cyber adversaries, though it isn't clear...

A suspected China-based threat actor has been linked to a series of cyber attacks targeting high-profile organizations in Southeast Asia since at least October 2023. The espionage campaign...

No word yet on who was snooped on. Any bets? Chinese cyberspies recorded "very senior" US political figures' calls, according to White House security boss Anne Neuberger.…

A 59-year-old U.S. citizen who immigrated from the People's Republic of China (PRC) has been sentenced to four years in prison for conspiring to act as a spy for the country and sharing sensitive...

Senate Intelligence Committee chair says his 'hair is on fire' as execs front the White House The Biden administration on Friday hosted telco execs to chat about China's recent attacks on the...

Beijing's propaganda buddies aren't just using social media Google’s Threat Intelligence Group has blocked a network China-related firms from its search results for operating fake news services...

Government agencies and non-governmental organizations in the United States have become the target of a nascent China state threat actor known as Storm-2077. The adversary, believed to be active...
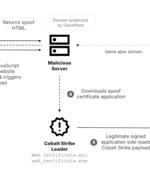
A China-linked nation-state group called TAG-112 compromised Tibetan media and university websites in a new cyber espionage campaign designed to facilitate the delivery of the Cobalt Strike...

A new China-linked cyber espionage group has been attributed as behind a series of targeted cyber attacks targeting telecommunications entities in South Asia and Africa since at least 2020 with...