Security News

Microsoft is now using a Windows driver to prevent users from changing the Windows 10 and Windows 11 default browser manually or through software. SetDefaultBrowser works similarly but is only for changing the default browser in Windows.

Browser fingerprinting is one of many tactics phishing site authors use to evade security checks and lengthen the lifespan of malicious campaigns. While browser fingerprinting has been used by legitimate organizations to uniquely identify web browsers for nearly 15 years, it is now also commonly exploited by cybercriminals: a recent study shows one in four phishing sites using some form of this technique.

As SaaS applications dominate the business landscape, organizations need optimized network speed and robust security measures. Many of them have been turning to SASE, a product category that...
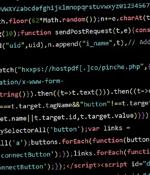
Threat actors are conducting brute-force attacks against WordPress sites by leveraging malicious JavaScript injections, new findings from Sucuri reveal. The attacks, which take the form of...

Hackers are conducting widescale attacks on WordPress sites to inject scripts that force visitors' browsers to bruteforce passwords for other sites. They then hack X accounts, create YouTube videos, or take out Google and X advertisements to promote the sites and steal visitor's cryptocurrency.

Brave Software is the next company to jump into AI, announcing a new privacy-preserving AI assistant called "Leo" is rolling out on the Android version of its browser through the latest release, version 1.63. Brave says its AI assistant stands out for its ability to provide high-quality, relevant answers with fewer errors, thanks to leveraging several advanced large-language models like Mixtral 8x7B, Claude Instant, and Llama 2 13B, with Mixtral set as the default for its multilingual capabilities and superior performance.

The DuckDuckGo browser has unveiled a new end-to-end encrypted Sync & Backup feature that lets users privately and securely synchronize their bookmarks, passwords, and Email Protection settings across multiple devices. The new feature is available on the latest version of the DuckDuckGo browser for Windows, macOS, iOS, and Android, so syncing can only work between devices running these operating systems.

Cybersecurity researchers have discovered a new Java-based "sophisticated" information stealer that uses a Discord bot to exfiltrate sensitive data from compromised hosts. The malware,...

A credit card or PayPal account is required for purchase. You will be billed the total shown above and you will receive a receipt via email once your payment is processed.

Security stakeholders have come to realize that the prominent role the browser has in the modern corporate environment requires a re-evaluation of how it is managed and protected. While not...