Security News

A team of security researchers has disclosed new side-channel vulnerabilities in modern Apple processors that could steal sensitive information from web browsers. [...]

Microsoft has announced that Game Assist, its recently unveiled in-game browser, is now also available in preview for Microsoft Edge Stable users. [...]

A recent campaign targeting browser extensions illustrates that they are the next frontier in identity attacks. Learn more about these attacks from LayerX Security and how to receive a free...

News has been making headlines over the weekend of the extensive attack campaign targeting browser extensions and injecting them with malicious code to steal user credentials. Currently, over 25...

Mandiant has identified a novel method to bypass contemporary browser isolation technology and achieve command-and-control C2 operations. [...]

In an effort to turn the tide, Mozilla is testing a fresh approach that could persuade more people to switch their default browser on Windows during the installation of the browser. [...]

Mozilla is testing a fresh approach that could persuade more people to switch their default browser on Windows. [...]

The rise of SaaS and cloud-based work environments has fundamentally altered the cyber risk landscape. With more than 90% of organizational network traffic flowing through browsers and web...
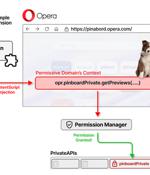
A now-patched security flaw in the Opera web browser could have enabled a malicious extension to gain unauthorized, full access to private APIs. The attack, codenamed CrossBarking, could have made...

Microsoft has disclosed details about a now-patched security flaw in Apple's Transparency, Consent, and Control (TCC) framework in macOS that has likely come under exploitation to get around a...