Security News

Just an FYI, like Generative AI assistants packaged up as browser extensions harvest personal data with minimal safeguards, researchers warn.…

Traditional Data Loss Prevention (DLP) solutions weren't built for today's browser-driven workplace. Now sensitive data moves moves through SaaS apps, AI tools, and personal accounts, bypassing...
Cybersecurity researchers have demonstrated a novel technique that allows a malicious web browser extension to impersonate any installed add-on. "The polymorphic extensions create a pixel perfect...

The FakeUpdate malware campaigns are increasingly becoming muddled, with two additional cybercrime groups tracked as TA2726 and TA2727, running campaigns that push a new macOS infostealer malware...
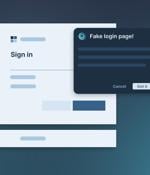
For years, defensive security strategies have focused on three core areas: network, endpoint, and email. Meanwhile, the browser, sits across all of them. This article examines three key areas...

Cybersecurity researchers are alerting to a new campaign that leverages web injects to deliver a new Apple macOS malware known as FrigidStealer. The activity has been attributed to a previously...

Researchers warn of rising macOS-targeted attacks as hackers exploit fake updates to bypass security. FrigidStealer malware highlights growing enterprise risks.

The North Korea-linked nation-state hacking group known as Kimsuky has been observed conducting spear-phishing attacks to deliver an information stealer malware named forceCopy, according to new...

Microsoft says it improved the contrast of text rendered in all Chromium-based web browsers on Windows, making it more readable on some displays. [...]

Google announced that the Chrome Sync feature will be discontinued in early 2025 for Chrome versions older than four years. [...]