Security News

The new PyScript project lets you embed Python programs directly in HTML pages and execute them within the browser without any server-based requirements. "PyScript is a framework that allows users to create rich Python applications in the browser using a mix of Python with standard HTML." explains Anaconda in a recent blog post.

Microsoft has released the Windows 11 KB5012592 cumulative update with security updates, quality improvements, and a fix that makes it easier to switch your default browser. KB5012592 is a mandatory cumulative update as it contains the April 2022 Patch Tuesday security updates for vulnerabilities discovered in previous months.

Instead, you can turn to a lesser known but more privacy-minded browser, and one candidate is the Ghostery Dawn browser. Made by the people behind the Ghostery browser privacy extension, Dawn tries to limit the information that is typically monitored and recorded when you use one of the major browsers.

Browser in the browser attacks consist of simulating a browser window within the browser to spoof a legitimate domain. The principle is pretty straightforward: The user connects to a website, which in turn opens a new browser window that asks for Google, Apple, Microsoft or other third parties' credentials, to allow the user to log in.

A Belarusian threat actor known as Ghostwriter has been spotted leveraging the recently disclosed browser-in-the-browser technique as part of their credential phishing campaigns exploiting the ongoing Russo-Ukrainian conflict. The method, which masquerades as a legitimate domain by simulating a browser window within the browser, makes it possible to mount convincing social engineering campaigns.

The novel phishing technique, described last week by a penetration tester and security researcher who goes by the handle mr. The concocted popups simulate a browser window within the browser, spoofing a legitimate domain and making it possible to stage convincing phishing attacks.
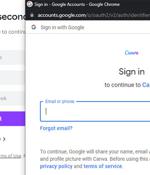
A novel phishing technique called browser-in-the-browser attack can be exploited to simulate a browser window within the browser in order to spoof a legitimate domain, thereby making it possible to stage convincing phishing attacks. "Combine the window design with an iframe pointing to the malicious server hosting the phishing page, and it's basically indistinguishable," mrd0x said in a technical write-up published last week.

A phishing kit has been released that allows red teamers and wannabe cybercriminals to create effective single sign-on phishing login forms using fake Chrome browser windows. Threat actors have attempted to create these fake SSO windows using HTML, CSS, and JavaScript in the past, but there is usually something a little off about the windows, making them look suspicious.

Bypassing defenses built into the user's browser to fool them into trusting a malicious page tends to be difficult in the absence of an exploitable vulnerability, thanks to browser security mechanisms including Content Security Policy settings and the Same-origin policy security model. The BitB attack extends this technique by creating an entirely fabricated browser window, including trust signals like a locked padlock icon and a known URL. You think you're seeing a real popup window, but it's actually just faked within the page, and ready to capture your credentials.
Meta Platforms' WhatsApp and Cloudflare have banded together for a new initiative called Code Verify to validate the authenticity of the messaging service's web app on desktop computers. Available in the form of a Chrome and Edge browser extension, the open-source add-on is designed to "Automatically verif[y] the authenticity of the WhatsApp Web code being served to your browser," Facebook said in a statement.