Security News

A novel credential-stealing malware called Zaraza bot is being offered for sale on Telegram while also using the popular messaging service as a command-and-control. "Zaraza bot targets a large number of web browsers and is being actively distributed on a Russian Telegram hacker channel popular with threat actors," cybersecurity company Uptycs said in a report published last week.

Cryptocurrency thieves are targeting users of Chromium-based browsers - Google Chrome, Microsoft Edge, Brave Browser, and Opera - with an extension that steals credentials and can grab multi-factor authentication codes. Dubbed Rilide by Trustwave researchers, the extension mimics the legitimate Google Drive extension while, in the background, it disables the Content Security Policy, collects system information, exfiltrates browsing history, takes screenshots, and injects malicious scripts.

Security researchers discovered a new malicious browser extension called Rilide, that targets Chromium-based products like Google Chrome, Brave, Opera, and Microsoft Edge. Researchers at Trustwave SpiderLabs found that Rilide mimicked benign Google Drive extensions to hide in plain sight while abusing built-in Chrome functionalities.
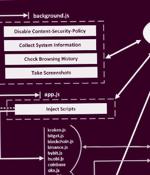
Chromium-based web browsers are the target of a new malware called Rilide that masquerades itself as a seemingly legitimate extension to harvest sensitive data and siphon cryptocurrency. "Rilide malware is disguised as a legitimate Google Drive extension and enables threat actors to carry out a broad spectrum of malicious activities, including monitoring."

Clipboard-injector malware disguised as Tor browser installers has been used to steal about $400,000 in cryptocurrency from nearly 16,000 users worldwide so far in 2023, according to Kaspersky researchers. "The Tor Project called to help keep Russian users connected to Tor to circumvent censorship," Vitaly Kamluk, head of Kaspersky's Global Research and Analysis Team for APAC, wrote in a blog about the clipper malware.
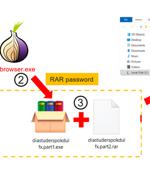
Trojanized installers for the TOR anonymity browser are being used to target users in Russia and Eastern Europe with clipper malware designed to siphon cryptocurrencies since September 2022. "Clipboard injectors can be silent for years, show no network activity or any other signs of presence until the disastrous day when they replace a crypto wallet address," Vitaly Kamluk, director of global research and analysis team for APAC at Kaspersky, said.

A surge of trojanized Tor Browser installers targets Russians and Eastern Europeans with clipboard-hijacking malware that steals infected users' cryptocurrency transactions. While these malicious Tor installers target countries worldwide, Kaspersky says that most are targeting Russia and Eastern Europe.

Google has stepped in to remove a bogus Chrome browser extension from the official Web Store that masqueraded as OpenAI's ChatGPT service to harvest Facebook session cookies and hijack the accounts. The "ChatGPT For Google" extension, a trojanized version of a legitimate open source browser add-on, attracted over 9,000 installations since March 14, 2023, prior to its removal.

Morphisec, a security solution provider based in Israel, has reported that an advanced information stealer malware dubbed SYS01 is aimed at stealing access to Facebook business accounts and Chromium-based browsers' credentials. Morphisec's researcher has also seen the SYS01 malware attack critical government infrastructure employees, manufacturing companies and other industries.

The report also details the top browser security threats of 2022, which include phishing attacks via high reputation domains, malware distribution via file sharing systems, data leakage exploiting personal browser profiles, outdated browsers, compromised passwords, vulnerable unmanaged devices, high-risk extensions, shadow IT, and account takeovers with phishing credentials. In addition to the stats and analysis of the prominent threats, the report provides a retrospect of the main news stories that left a mark in the world of browser security in 2022.