Security News

The U.S. Treasury Department has sanctioned a cybercrime network comprising three Chinese nationals and three Thailand-based companies linked to a massive botnet controlling a residential proxy service known as "911 S5.". Researchers at the Canadian University of Sherbrooke revealed almost two years ago, in June 2022, that this illegitimate residential proxy service lured potential victims by offering free VPN services to install malware designed to add their IP addresses to the 911 S5 botnet.

The threat actors behind the CatDDoS malware botnet have exploited over 80 known security flaws in various software over the past three months to infiltrate vulnerable devices and co-opt them into...
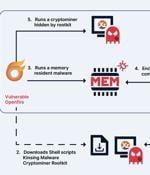
The cryptojacking group known as Kinsing has demonstrated its ability to continuously evolve and adapt, proving to be a persistent threat by swiftly integrating newly disclosed vulnerabilities to...

In many cases, Ebury operators could gain full access to large servers of ISPs and well-known hosting providers. "We have documented cases where the infrastructure of hosting providers was compromised by Ebury. In these cases, we have seen Ebury being deployed on servers rented out by those providers, with no warning to the lessees. This resulted in cases where the Ebury actors were able to compromise thousands of servers at once," says Marc-Etienne M. Léveillé, the ESET researcher who investigated Ebury for more than a decade.
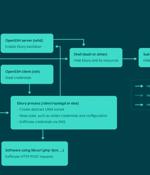
A malware botnet called Ebury is estimated to have compromised 400,000 Linux servers since 2009, out of which more than 100,000 were still compromised as of late 2023. The findings come from...

A malware botnet known as 'Ebury' has infected almost 400,000 Linux servers since 2009, with roughly 100,000 still compromised as of late 2023. "While 400,000 is a massive number, it's important to mention that this is the number of compromises over the course of almost 15 years. Not all of those machines were compromised at the same time," explains ESET. "There is a constant churn of new servers being compromised while others are being cleaned up or decommissioned. The data at our disposal doesn't indicate when the attackers lost access to the systems, so it's difficult to know the size of the botnet at any specific point in time."

Since April, millions of phishing emails have been sent through the Phorpiex botnet to conduct a large-scale LockBit Black ransomware campaign. The LockBit Black encryptor deployed in these attacks is likely built using the LockBit 3.0 builder leaked by a disgruntled developer on Twitter in September 2022.

Two recently disclosed security flaws in Ivanti Connect Secure (ICS) devices are being exploited to deploy the infamous Mirai botnet. That's according to findings from Juniper Threat Labs, which...

A never-before-seen botnet called Goldoon has been observed targeting D-Link routers with a nearly decade-old critical security flaw with the goal of using the compromised devices for further...

The U.S. Justice Department charged Moldovan national Alexander Lefterov, the owner and operator of a large-scale botnet that infected thousands of computers across the United States. Infected computers could also be accessed directly using a hidden virtual network computing server without the owners' knowledge.