Security News
"Now it is significantly harder to separate the wheat from the chaff and discover the real C&C servers among thousands of legitimate domains used by Xloader as a smokescreen," Israeli cybersecurity company Check Point said. The latest findings from Check Point build on a previous report from Zscaler in January 2022, which revealed the inner workings of the malware's C&C network encryption and communication protocol, noting its use of decoy servers to conceal the legitimate server and evade malware analysis systems.

Threat analysts have spotted a new version of the XLoader botnet malware that uses probability theory to hide its command and control servers, making it difficult to disrupt the malware's operation. XLoader already camouflaged its actual command and control servers in version 2.3 by hiding the real domain name in a configuration that includes 63 decoys.
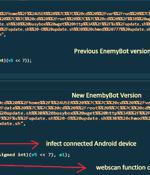
A nascent Linux-based botnet named Enemybot has expanded its capabilities to include recently disclosed security vulnerabilities in its arsenal to target web servers, Android devices, and content management systems. "The malware is rapidly adopting one-day vulnerabilities as part of its exploitation capabilities," AT&T Alien Labs said in a technical write-up published last week.

A fresh look at the Fronton DDoS-focused botnet reveals the criminal tool has more capabilities than previously known. The Fronton botnet first made the headline in March 2020.

Microsoft has sounded the alarm on DDoS malware called XorDdos that targets Linux endpoints and servers. Over the last six months, Microsoft threat researchers say they've witnessed a 254 percent spike in the malware's activity.

"This system includes a web-based dashboard known as SANA that enables a user to formulate and deploy trending social media events en masse. The system creates these events that it refers to as Инфоповоды, 'newsbreaks,' utilizing the botnet as a geographically distributed transport." The existence of Fronton, an IoT botnet, became public knowledge following revelations from BBC Russia and ZDNet in March 2020 after a Russian hacker group known as Digital Revolution published documents that it claimed were obtained after breaking into a subcontractor to the FSB, the Federal Security Service of the Russian Federation.

The latest variant of the Sysrv botnet malware is menacing Windows and Linux systems with an expanded list of vulnerabilities to exploit, according to Microsoft. The strain, which Microsoft's Security Intelligence team calls Sysrv-K, scans the internet for web servers that have security holes, such as path traversal, remote file disclosure, and arbitrary file download bugs, that can be exploited to infect the machines.

Unpatched vulnerabilities in the Spring Framework and WordPress plugins are being exploited by cybercriminals behind the Sysrv botnet to target Linux and Windows systems. The botnet variant is being called Sysrv-K by Microsoft Security Intelligence researchers that posted a thread on Twitter revealing details of the botnet variant.
Microsoft is warning of a new variant of the srv botnet that's exploiting multiple security flaws in web applications and databases to install coin miners on both Windows and Linux systems. The tech giant, which has called the new version Sysrv-K, is said to weaponize an array of exploits to gain control of web servers.

Microsoft says the Sysrv botnet is now exploiting vulnerabilities in the Spring Framework and WordPress to ensnare and deploy cryptomining malware on vulnerable Windows and Linux servers. "The new variant, which we call Sysrv-K, sports additional exploits and can gain control of web servers" by exploiting various vulnerabilities, the Microsoft Security Intelligence team said in a Twitter thread. "These vulnerabilities, which have all been addressed by security updates, include old vulnerabilities in WordPress plugins, as well as newer vulnerabilities like CVE-2022-22947."