Security News

Security researchers have pinned a DDoS botnet that's infected potentially millions of smart TVs and set-top boxes to an eight-year-old cybercrime syndicate called Bigpanzi. "The potential for Bigpanzi-controlled TVs and STBs to broadcast violent, terroristic, or pornographic content, or to employ increasingly convincing AI-generated videos for political propaganda, poses a significant threat to social order and stability," said researchers at Chinese security biz Qianxin.

A previously unknown cybercrime syndicate named 'Bigpanzi' has been making significant money by infecting Android TV and eCos set-top boxes worldwide since at least 2015. Bigpanzi infects the devices via firmware updates or backdoored apps the users are tricked into installing themselves, as highlighted in a September 2023 report by Dr. Web.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) warned that threat actors deploying the AndroxGh0st malware are creating a botnet for...

Crooks are exploiting years-old vulnerabilities to deploy Androxgh0st malware and build a cloud-credential stealing botnet, according to the FBI and the Cybersecurity and Infrastructure Security Agency. Miscreants deploying Androxgh0st like to use three old CVEs in these credential-stealing attacks: CVE-2017-9841, a command injection vulnerability in PHPUnit; CVE-2018-15133, an insecure deserialization bug in the Laravel web application framework that leads to remote code execution; and CVE-2021-41773, a path traversal vulnerability in Apache HTTP Server that also leads to remote code execution.

CISA and the FBI warned today that threat actors using Androxgh0st malware are building a botnet focused on cloud credential theft and using the stolen information to deliver additional malicious payloads. "Androxgh0st is a Python-scripted malware primarily used to target.env files that contain confidential information, such as credentials for various high profile applications," the two agencies cautioned.

About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I've been writing about security issues on my blog since 2004, and in my monthly newsletter since 1998.

A new Mirai-based botnet called NoaBot is being used by threat actors as part of a crypto mining campaign since the beginning of 2023. “The capabilities of the new botnet, NoaBot, include a...

A Mirai-based botnet named 'InfectedSlurs' is exploiting a remote code execution vulnerability in QNAP VioStor NVR devices to hijack and make them part of its DDoS swarm. The second zero-day vulnerability in the botnet's attacks is CVE-2023-47565, a high-severity OS command injection impacting QNAP VioStor NVR models running QVR firmware 4.x. QNAP published an advisory on December 7, 2023, explaining that the previously unknown issue was fixed in QVR firmware 5.x and later, which is available to all actively supported models.
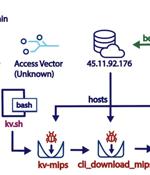
A new botnet consisting of firewalls and routers from Cisco, DrayTek, Fortinet, and NETGEAR is being used as a covert data transfer network for advanced persistent threat actors, including the...

The Chinese state-sponsored APT hacking group known as Volt Typhoon has been linked to a sophisticated botnet named 'KV-botnet' since at least 2022 to attack SOHO routers in high-value targets. Volt Typhoon commonly targets routers, firewalls, and VPN devices to proxy malicious traffic so it blends with legitimate traffic to remain undetected.