Security News

A custom Flipper Zero firmware called 'Xtreme' has added a new feature to perform Bluetooth spam attacks on Android and Windows devices. The main idea behind the spam attack is to use Flipper Zero's wireless communication capabilities to spoof advertising packets and transmit them to devices in range of pairing and connection requests.

Turns out pumps at gas stations are controlled via Bluetooth, and that the connections are insecure. No details in the article, but it seems that it's easy to take control of the pump and have it dispense gas without requiring payment.

The Flipper Zero portable wireless pen-testing and hacking tool can be used to aggressively spam Bluetooth connection messages at Apple iOS devices, such as iPhones and iPads. Apple devices supporting Bluetooth Low Energy technology utilize advertising packets to announce their presence to other devices.
Apple and Google have come together to develop an industry specification to prevent "Unwanted tracking," otherwise known as stalking, via Bluetooth location tracking tags. Though Tile has been selling Bluetooth Low Energy wireless tracking tags for a decade, it wasn't until 2021, when Samsung introduced its Galaxy SmartTag and Apple introduced its AirTag, that reports of abuse of the devices became commonplace.
Apple and Google have joined forces to push for adopting new industry standards designed to stop stalking via Bluetooth-enabled location-tracking devices. "The first-of-its-kind specification will allow Bluetooth location-tracking devices to be compatible with unauthorized tracking detection and alerts across iOS and Android platforms," Apple and Google said in coordinated press releases published today.

We've always known that phones-and the people carrying them-can be uniquely identified from their Bluetooth signatures, and that we need security techniques to prevent that. Computer scientists at the University of California San Diego proved in a study published May 24 that minute imperfections in phones caused during manufacturing create a unique Bluetooth beacon, one that establishes a digital signature or fingerprint distinct from any other device.

Researchers warn Bluetooth signals can be used to track device owners via a unique fingerprinting of the radio signal. The paper suggests that minor manufacturing imperfections in hardware are unique with each device, and cause measurable distortions which can be used as a "Fingerprint to track a specific device".
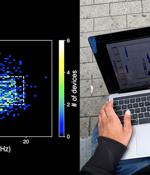
A new research undertaken by a group of academics from the University of California San Diego has revealed for the first time that Bluetooth signals can be fingerprinted to track smartphones. "To perform a physical-layer fingerprinting attack, the attacker must be equipped with a Software Defined Radio sniffer: a radio receiver capable of recording raw IQ radio signals," the researchers said in a new paper titled "Evaluating Physical-Layer BLE Location Tracking Attacks on Mobile Devices."

There are technological and expertise hurdles that a miscreant would have to clear today to track a person through the Bluetooth signals in their devices, they wrote. The researchers - who hail from the school's departments of Computer Science and Engineering and Electrical and Computer Engineering - pointed to the applications governments added to Apple iOS and Android devices used in the COVID-19 pandemic that send out constant Bluetooth signals - or beacons - for contact-tracing efforts.

Kali Linux 2022.2 released: Desktop enhancements, tweaks for the terminal, new tools, and more!Offensive Security has released Kali Linux 2022.2, the latest version of its popular penetration testing and digital forensics platform. VMware issues critical fixes, CISA orders federal agencies to act immediatelyVMware has released patches for a privately reported critical vulnerability in VMware's Workspace ONE Access, VMware Identity Manager, vRealize Lifecycle Manager, vRealize Automation, and VMware Cloud Foundation products, and is urging administrators to patch or mitigate immediately, because "The ramifications of this vulnerability are serious."