Security News
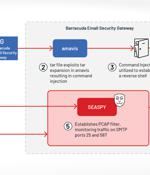
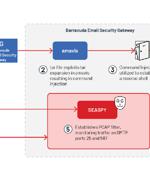
The U.S. Cybersecurity and Infrastructure Security Agency on Friday disclosed details of a "Novel persistent backdoor" called SUBMARINE deployed by threat actors in connection with the hack on Barracuda Email Security Gateway appliances. The findings come from an analysis of malware samples obtained from an unnamed organization that had been compromised by threat actors exploiting a critical flaw in ESG devices, CVE-2023-2868, which allows for remote command injection.

CISA says new malware known as Submarine was used to backdoor Barracuda ESG (Email Security Gateway) appliances by exploiting a now-patched zero-day bug. [...]

Email and network security firm Barracuda is working to fix an ongoing issue that triggers invalid login errors and prevents Email Gateway Defense users from signing into their accounts. "We are investigating login problems seen by users and have identified the problem. We are working on fixing the issue with a tentative timeline for the fix to be released on or before July 14th," Barracuda says.

Chinese spies are behind the data-stealing malware injected into Barracuda's Email Security Gateway devices globally as far back as October 2022, according to Mandiant. Mandiant, who has been working with Barracuda to investigate the exploit used and the malware subsequently deployed, today identified a China-based threat group it tracks as UNC4841, and said the snoops targeted a "Subset" of Barracuda ESG appliances across several regions and sectors.
A suspected China-nexus threat actor dubbed UNC4841 has been linked to the exploitation of a recently patched zero-day flaw in Barracuda Email Security Gateway appliances since October 2022. "UNC4841 is an espionage actor behind this wide-ranging campaign in support of the People's Republic of China," Google-owned Mandiant said in a new report published today, describing the group as "Aggressive and skilled."

A suspected pro-China hacker group tracked by Mandiant as UNC4841 has been linked to data-theft attacks on Barracuda ESG appliances using a now-patched zero-day vulnerability. "Due to the sophistication displayed by UNC4841 and lack of full visibility into all compromised appliances, Barracuda has elected to replace and not reimage the appliance from the recovery partition out of an abundance of caution," John Palmisano, Mandiant Incident Response Manager - Google Cloud, told BleepingComputer.

Barracuda Networks is urging customers running phyisical Email Security Gateway appliances to replace them immediately, "Regardless of patch version level." Barracuda has identified a critical vulnerability in their ESG appliances on May 19, 2023, and pushed a patch to them all on the following day.

Barracuda has now told customers to "Immediately" replace infected Email Security Gateway appliances - even if they have received a patch to fix a critical bug under exploit. Barracuda pushed a patch to all affected products the day after discovering the issue, but that wasn't quick enough.

Enterprise security company Barracuda is now urging customers who were impacted by a recently disclosed zero-day flaw in its Email Security Gateway appliances to immediately replace them. "Impacted ESG appliances must be immediately replaced regardless of patch version level," the company said in an update, adding its "Remediation recommendation at this time is full replacement of the impacted ESG.".

Email and network security company Barracuda warns customers they must replace Email Security Gateway appliances hacked in attacks targeting a now-patched zero-day vulnerability. "Impacted ESG appliances must be immediately replaced regardless of patch version level," the company warned in an update to the initial advisory issued on Tuesday.