Security News

Barracuda has revealed that Chinese threat actors exploited a new zero-day in its Email Security Gateway (ESG) appliances to deploy backdoor on a "limited number" of devices. Tracked...

Network and email security firm Barracuda says it remotely patched all active Email Security Gateway appliances on December 21 against a zero-day bug exploited by UNC4841 Chinese hackers. The company deployed a second wave of security updates a day later on already compromised ESG appliances where the attackers deployed SeaSpy and Saltwater malware.

Nearly a third of organizations compromised by Chinese cyberspies via a critical bug in some Barracuda Email Security Gateways were government units, according to Mandiant. Mandiant continues to recommend people dump and replace their at-risk Barracuda equipment.
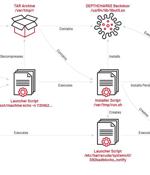
A suspected Chinese-nexus hacking group exploited a recently disclosed zero-day flaw in Barracuda Networks Email Security Gateway appliances to breach government, military, defense and aerospace, high-tech industry, and telecom sectors as part of a global espionage campaign. What's more, FOXTROT shares overlaps with an open-source rootkit called Reptile, which has been extensively used by multiple Chinese hacking crews in recent months.

Suspected Chinese hackers disproportionately targeted and breached government and government-linked organizations worldwide in recent attacks targeting a Barracuda Email Security Gateway zero-day, with a focus on entities across the Americas. Barracuda warned customers that the vulnerability was being exploited to breach ESG appliances on May 20, when it also patched all vulnerable devices remotely.

The U.S. Federal Bureau of Investigation is warning that Barracuda Networks Email Security Gateway appliances patched against a recently disclosed critical flaw continue to be at risk of potential compromise from suspected Chinese hacking groups. It also deemed the fixes as "Ineffective" and that it "Continues to observe active intrusions and considers all affected Barracuda ESG appliances to be compromised and vulnerable to this exploit."

The FBI has warned owners of Barracuda Email Security Gateway appliances the devices are likely undergoing attack by snoops linked to China, and removing the machines from service remains the safest course of action. On Wednesday, the FBI pushed that recommendation in a flash alert [PDF] that stated it "Strongly advises all affected ESG appliances be isolated and replaced immediately."

The Federal Bureau of Investigation warned that patches for a critical Barracuda Email Security Gateway remote command injection flaw are "Ineffective," and patched appliances are still being compromised in ongoing attacks. Even though the Barracuda patched all appliances remotely and blocked the attackers' access to the breached devices on May 20, one day after the bug was identified, it also warned all customers on June 7 that they must replace all impacted appliances immediately, likely because it couldn't ensure the complete removal of malware deployed in the attacks.

The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has discovered a new backdoor malware named 'Whirlpool' used in attacks on compromised Barracuda Email Security Gateway (ESG) devices. [...]

The Cybersecurity and Infrastructure Agency has published an analysis report on the backdoors dropped by attackers exploiting CVE-2023-2868, a remote command injection vulnerability in Barracuda Email Security Gateway appliances. In late May, Barracuda warned that attackers have been exploiting the vulnerability in Barracuda Networks' ESG physical appliances.