Security News

A malicious Python package named 'fabrice' has been present in the Python Package Index (PyPI) since 2021, stealing Amazon Web Services credentials from unsuspecting developers. [...]

Cybersecurity researchers have discovered a malicious package on the Python Package Index (PyPI) that has racked up thousands of downloads for over three years while stealthily exfiltrating...

AWS offers a comprehensive suite of security tools to help organizations manage compliance, protect sensitive data, and detect threats within their environments. From AWS Security Hub and Amazon...

Remember Bucket Monopoly? Yeah, it gets worse Amazon Web Services has fixed a flaw in its open source Cloud Development Kit that, under the right conditions, could allow an attacker to hijack a...
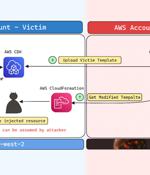
Cybersecurity researchers have disclosed a security flaw impacting Amazon Web Services (AWS) Cloud Development Kit (CDK) that could have resulted in an account takeover under specific...

Multiple popular mobile applications for iOS and Android come with hardcoded, unencrypted credentials for cloud services like Amazon Web Services (AWS) and Microsoft Azure Blob Storage, exposing...
As many as 15,000 applications using Amazon Web Services' (AWS) Application Load Balancer (ALB) for authentication are potentially susceptible to a configuration-based issue that could expose them...

If you needed yet another reminder of what happens when security basics go awry It's a good news day for organizations that don't leave their AWS environment files publicly exposed because infosec...

As cloud infrastructure becomes the backbone of modern enterprises, ensuring the security of these environments is paramount. With AWS (Amazon Web Services) still being the dominant cloud it is...
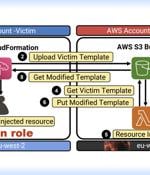
Central to the issue, dubbed Bucket Monopoly, is an attack vector referred to as Shadow Resource, which, in this case, refers to the automatic creation of an AWS S3 bucket when using services like CloudFormation, Glue, EMR, SageMaker, ServiceCatalog, and CodeStar. An attacker could take advantage of this behavior to set up buckets in unused AWS regions and wait for a legitimate AWS customer to use one of the susceptible services to gain covert access to the contents of the S3 bucket.