Security News

From sophisticated nation-state-sponsored intrusions to opportunistic malware campaigns, cyber attacks manifest in various forms, targeting vulnerabilities in networks, applications, and user behavior. The consequences of successful cyber attacks can be severe, ranging from financial losses and reputational damage to potential legal ramifications.

Ransomware attacks targeting VMware ESXi and other virtual machine platforms are wreaking havoc among the enterprise, causing widespread disruption and loss of services. Panera's massive IT outage last month that took down internal systems, the website, mobile apps, and phones was caused by a ransomware attack encrypting the company's virtual machines.
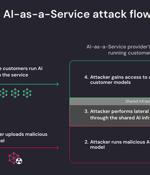
New research has found that artificial intelligence (AI)-as-a-service providers such as Hugging Face are susceptible to two critical risks that could allow threat actors to escalate privileges,...

Panera Bread's recent week-long outage was caused by a ransomware attack, according to people familiar with the matter and emails seen by BleepingComputer. Panera has not responded to multiple requests for comments about the outage and the attack.

Newly discovered HTTP/2 protocol vulnerabilities called "CONTINUATION Flood" can lead to denial of service attacks, crashing web servers with a single TCP connection in some implementations. HTTP/2 is an update to the HTTP protocol standardized in 2015, designed to improve web performance by introducing binary framing for efficient data transmission, multiplexing to allow multiple requests and responses over a single connection, and header compression to reduce overhead. The new CONTINUATION Flood vulnerabilities were discovered by researcher Barket Nowotarski, who says that it relates to the use of HTTP/2 CONTINUATION frames, which are not properly limited or checked in many implementations of the protocol.

Today's malware is not just about causing immediate damage; some programs get embedded within systems to siphon off data over time, disrupt operations strategically, or lay the groundwork for massive, coordinated attacks. Read on to get the lowdown on recent high-profile malware attacks along with strategies to help limit malware risks at your organization.

New research has unveiled a vulnerability within the HTTP/2 protocol, known as HTTP/2 CONTINUATION Flood, that allows for denial-of-service (DoS) attacks. This issue, discovered by security researcher Bartek Nowotarski and reported to CERT/CC on January 25, 2024, arises from improper handling of CONTINUATION frames—a component used to transmit extended header lists within a single stream. CERT/CC's advisory highlights that attackers exploiting this vulnerability could send continuous CONTINUATION frames without concluding them with an END_HEADERS flag, leading to potential server crashes or significant performance drops due to out-of-memory conditions or CPU exhaustion.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

What are the most common and dangerous cyber threats facing the healthcare sector in 2024? Cyber threats haven't necessarily changed, but they've become more frequent in healthcare.
There is an urgent need to secure tactical, operational, and strategic critical assets from the edge to the core. In this Help Net Security video, Geoffrey Mattson, CEO of Xage Security, discusses the steps enterprises and critical infrastructure must take to improve their environments from for-profit and nation-state attacks.