Security News
A distributed denial-of-service attack earlier this year takes the top spot for the largest such incident, peaking at 17.2 million requests per second. The attack was recorded by Cloudflare's DDoS protection systems and accounted for almost 70% of all average rate for legitimate HTTP traffic for the second quarter of 2021.
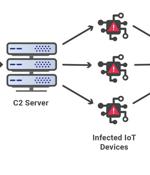
Web infrastructure and website security company Cloudflare on Thursday disclosed that it mitigated the largest ever volumetric distributed denial of service attack recorded to date. "Within seconds, the botnet bombarded the Cloudflare edge with over 330 million attack requests," the company noted, at one point reaching a record high of 17.2 million requests-per-second, making it three times bigger than previously reported HTTP DDoS attacks.
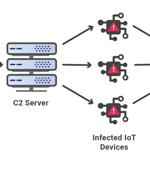
Web infrastructure and website security company Cloudflare on Thursday disclosed that it mitigated the largest ever volumetric distributed denial of service attack recorded to date. "Within seconds, the botnet bombarded the Cloudflare edge with over 330 million attack requests," the company noted, at one point reaching a record high of 17.2 million requests-per-second, making it three times bigger than previously reported HTTP DDoS attacks.

There are four steps to analyzing how prepared you are for a ransomware attack. Such analysis roughly breaks down as follows: How easy it is to break into your environment in the first place; given an initial toe-hold, how difficult is it for an attacker to escalate privilege, move laterally and get access to data and systems critical to your business; do you have a handle on data which would warrant a substantial ransom to prevent public disclosure and how easy would it be to exfiltrate large amounts of data from your environment without detection; and how confident are you of your ability to quickly restore your environment from backups?

A second unofficial patch for the Windows PetitPotam NTLM relay attack has been released to fix further issues not addressed by Microsoft's official security update. In July, security researcher GILLES Lionel, aka Topotam, disclosed a new technique called 'PetitPotam' that performs unauthenticated forced authentication on domain controllers using various functions in the MS-EFSRPC API. Microsoft's security update is not complete.

Cisco said that unauthenticated attackers could bypass TLS inspection filtering tech in multiple products to exfiltrate data from previously compromised servers inside customers' networks. The threat actors can exploit a vulnerability in the Server Name Identification request filtering impacting 3000 Series Industrial Security Appliances, Firepower Threat Defense, and Web Security Appliance products.

Absolute Software announced a research revealing the significant management and security challenges faced by K-12 education IT teams with the rise in digital learning and widespread adoption of 1:1 device programs. The report underscores how increased device mobility and complexity are leaving schools increasingly vulnerable to security risks and potential attacks.

Overall, the first half of 2021 shows a 22 percent increase in the volume of phishing attacks over the same time period last year, PhishLabs reveals. The impact of phishing attacks in H1 2021 Crypto is fully in attackers' sights: This category experienced an increase of phishing attacks 10 times greater than the previous quarter in 2021.

The Cybersecurity Infrastructure and Security Agency and BlackBerry warned in separate alerts Tuesday that threat actors can take over or launch denial of service attacks on devices and critical infrastructure by exploiting what are called BadAlloc bugs tied to BlackBerry's QNX operating system. QNX is a real-time OS, used in embedded systems such as automobiles, medical devices and handsets.

Tokio Marine Holdings, a multinational insurance holding company in Japan, announced this week that its Singapore branch, Tokio Marine Insurance Singapore, suffered a ransomware attack. As the largest property and casualty insurance group in Japan, Tokio Marine Holdings is an attractive target for cybercriminals, who can use the breach to find and compromise customers of the organization.