Security News
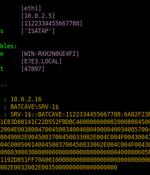
A new kind of Windows NTLM relay attack dubbed DFSCoerce has been uncovered that leverages the Distributed File System: Namespace Management Protocol to seize control of a domain. "Spooler service disabled, RPC filters installed to prevent PetitPotam and File Server VSS Agent Service not installed but you still want to relay ? Don't worry MS-DFSNM have your back," security researcher Filip Dragovic said in a tweet.

A new DFSCoerce Windows NTLM relay attack has been discovered that uses MS-DFSNM, Microsoft's Distributed File System, to completely take over a Windows domain. This service is vulnerable to NTLM relay attacks, which is when threat actors force, or coerce, a domain controller to authenticate against a malicious NTLM relay under an attacker's control.

Hertzbleed is a new side-channel attack that works against a variety of microprocressors. Deducing cryptographic keys by analyzing power consumption has long been an attack, but it's not generally viable because measuring power consumption is often hard.

Hartzbleed is a new side-channel attack that works against a variety of microprocressors. Deducing cryptographic keys by analyzing power consumption has long been an attack, but it's not generally viable because measuring power consumption is often hard.

This week, ech0raix ransomware has started targeting vulnerable QNAP Network Attached Storage devices again, according to user reports and sample submissions on the ID Ransomware platform. Ech0raix had hit QNAP customers in multiple large-scale waves starting with the summer of 2019 when the attackers brute-forced their way into Internet-exposed NAS devices.

Security researchers have noticed a new malicious spam campaign that delivers the 'Matanbuchus' malware to drop Cobalt Strike beacons on compromised machines. Cobalt Strike is a penetration testing suite that is frequently used by threat actors for lateral movement and to drop additional payloads.

A decentralized autonomous organization called Inverse Finance has been robbed of cryptocurrency somehow exchangeable for $1.2 million, just two months after being taken for $15.6 million. So Inverse Finance is counting it as bad debt rather than funds that need to be repaid to any individual.

Network-attached storage vendor QNAP once again warned customers on Friday to secure their devices against a new campaign of attacks pushing DeadBolt ransomware. "QNAP recently detected a new DeadBolt ransomware campaign. According to victim reports so far, the campaign appears to target QNAP NAS devices running QTS 4.x," QNAP said today.

Netacea released its report into how businesses are dealing with bot attacks. It reveals one key area where businesses are failing to tackle bot attacks - bots are going undiscovered for an average of 16 weeks, up two weeks from last year's findings.

Anker's central smart home device hub, Eufy Homebase 2, was vulnerable to three vulnerabilities, one of which is a critical remote code execution flaw. Homebase 2 is the video storage and networking gateway for all Anker's Eufy smart home devices, including video doorbells, indoor security cameras, smart locks, alarm systems, and more.