Security News

SMBs should focus on their attack surface and work on reducing it to the bare minimum required to operate their business. Understanding your attack surface is key to understanding what you are defending and how.

Cloud communications company Twilio says some of its customers' data was accessed by attackers who breached internal systems after stealing employee credentials in an SMS phishing attack. "On August 4, 2022, Twilio became aware of unauthorized access to information related to a limited number of Twilio customer accounts through a sophisticated social engineering attack designed to steal employee credentials," Twilio said over the weekend.

Deepfake attacks and cyber extortion are creating mounting risks. "In February VMware reported seeing a new type of malware deployed in one of the largest targeted attacks in history focused solely on the destruction of critical information and resources."This is part of a growing list of destructive malware deployed against Ukraine, as noted in a joint advisory the Cybersecurity and Infrastructure Security Agency and the FBI released this spring,'' the report stated.

Attackers abused open redirects on the websites of Snapchat and American Express in a series of phishing attacks to steal Microsoft 365 credentials. Open redirects are web app weaknesses that allow threat actors to use the domains of trusted organizations and websites as temporary landing pages to simplify phishing attacks.
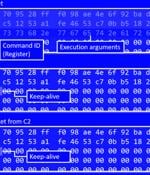
"This family borrows heavily from the original Mirai source code, but what separates it from other IoT malware families is its built-in capability to brute force credentials and gain access to SSH servers instead of Telnet as implemented in Mirai," Fortinet FortiGuard Labs said in a report. The malware, which gets its name from an embedded URL to a YouTube rap music video in an earlier version, is said to have amassed a growing collection of compromised SSH servers, with over 3,500 unique IP addresses used to scan and brute-force their way into the servers.

A nascent service called Dark Utilities has already attracted 3,000 users for its ability to provide command-and-control services with the goal of commandeering compromised systems. Users are provided an administrative panel to run commands on the machines under their control upon establishing an active C2 channel, effectively granting the attacker full access to the systems.

With the proliferation of mobile devices and hybrid work environments where employees often use their personal devices for work-related activities almost half of respondents of the Verizon Mobile Security Index 2022 said their organizations were subject to a security incident involving a mobile device that led to data loss, downtime or other negative outcome-a 22% increase over 2021's numbers. Despite these results, 36% of respondents said that mobile devices are of less interest to cybercriminals than other IT assets-an increase of six percentage points from the 2021 MSI report.

Ransomware has become more pervasive and more sophisticated, challenging organizations to combat attacks that occur at greater frequency and greater complexity. Among the respondents to the report,"2022 Impacts: Ransomware attacks and preparedness," one-third said that their organization is hit by a ransomware attempt at least weekly, with 9% reporting attacks more than once each day.

A new, large-scale phishing campaign has been observed using adversary-in-the-middle techniques to get around security protections and compromise enterprise email accounts. Opening the attachment via a web browser redirects the email recipient to the phishing page that masquerades as a login page for Microsoft Office, but not before fingerprinting the compromised machine to determine whether the victim is actually the intended target.

Other most impersonated legitimate apps by icon include 7-Zip, TeamViewer, CCleaner, Microsoft Edge, Steam, Zoom, and WhatsApp, an analysis from VirusTotal has revealed. "One of the simplest social engineering tricks we've seen involves making a malware sample seem a legitimate program," VirusTotal said in a Tuesday report.