Security News
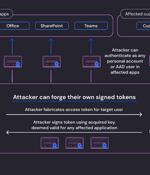
According to cloud security company Wiz, the inactive Microsoft account consumer signing key used to forge Azure Active Directory tokens to gain illicit access to Outlook Web Access and Outlook.com could also have allowed the adversary to forge access tokens for various types of Azure AD applications. Wiz's analysis fills in some of the blanks, with the company discovering that "All Azure personal account v2.0 applications depend on a list of 8 public keys, and all Azure multi-tenant v2.0 applications with Microsoft account enabled depend on a list of 7 public keys."

The exploitation of the Citrix NetScaler ADC zero-day vulnerability was first spotted by a critical infrastructure organization, who reported it to the Cybersecurity and Infrastructure Security Agency. "In June 2023, threat actors exploited this vulnerability as a zero-day to drop a webshell on a critical infrastructure organization's non-production environment NetScaler ADC appliance. The webshell enabled the actors to perform discovery on the victim's active directory and collect and exfiltrate AD data. The actors attempted to move laterally to a domain controller but network-segmentation controls for the appliance blocked movement," the agency shared in an advisory published on Thursday.

Several distributed denial-of-service botnets have been observed exploiting a critical flaw in Zyxel devices that came to light in April 2023 to gain remote control of vulnerable systems. "Through the capture of exploit traffic, the attacker's IP address was identified, and it was determined that the attacks were occurring in multiple regions, including Central America, North America, East Asia, and South Asia," Fortinet FortiGuard Labs researcher Cara Lin said.

The U.S. Cybersecurity and Infrastructure Security Agency issued an advisory on Thursday warning that the newly disclosed critical security flaw in Citrix NetScaler Application Delivery Controller and Gateway devices is being abused to drop web shells on vulnerable systems. "In June 2023, threat actors exploited this vulnerability as a zero-day to drop a web shell on a critical infrastructure organization's non-production environment NetScaler ADC appliance," the agency said.

As we entered 2023, the cybersecurity landscape witnessed an increase in sophisticated, high-volume attacks, according to Gcore. The maximum attack power rose from 600 to 800 Gbps. UDP flood attacks were most common and amounted to 52% of total attacks, while SYN flood accounted for 24%. In third place was TCP flood.

Two more security flaws have been disclosed in AMI MegaRAC Baseboard Management Controller software that, if successfully exploited, could allow threat actors to remotely commandeer vulnerable servers and deploy malware. "These new vulnerabilities range in severity from High to Critical, including unauthenticated remote code execution and unauthorized device access with superuser permissions," Eclypsium researchers Vlad Babkin and Scott Scheferman said in a report shared with The Hacker News.
An analysis of the indicators of compromise associated with the JumpCloud hack has uncovered evidence pointing to the involvement of North Korean state-sponsored groups, in a style that's reminiscent of the supply chain attack targeting 3CX. The findings come from SentinelOne, which mapped out the infrastructure pertaining to the intrusion to uncover underlying patterns. "The North Korean threat actors demonstrate a high level of creativity and strategic awareness in their targeting strategies," SentinelOne security researcher Tom Hegel told The Hacker News.

Two ransomware actors, ALPHV/BlackCat and Clop, have listed beauty company Estée Lauder on their data leak sites as a victim of separate attacks. In a Security Exchange Commission filing on Tuesday, The Estée Lauder Companies confirmed one of the attacks saying that the threat actor gained access to some of its systems and may have stolen data.

Adobe released an emergency ColdFusion security update that fixes critical vulnerabilities, including a fix for a new zero-day exploited in attacks. Adobe says the CVE-2023-38205 flaw was abused in limited attacks.

With cloud migration dramatically increasing the number of internal and external targets, prioritizing threats and managing your attack surface from an attacker's perspective has never been more important. First, it's important to understand that your attack surface is the sum of your digital assets that are 'exposed' - whether the digital assets are secure or vulnerable, known or unknown, in active use or not.