Security News

Inventive attackers are specifically targeting Mac systems, as seen with the "Geacon" Cobalt Strike tool attack. To understand the state of cybersecurity on the Mac, the Moonlock team, a dedicated group of MacPaw's researchers and engineers focused on the cybersecurity needs of Mac users, conducted a survey.

Google's security researcher Tavis Ormandy discovered a new vulnerability impacting AMD Zen2 CPUs that could allow a malicious actor to steal sensitive data, such as passwords and encryption keys, at a rate of 30KB/sec from each CPU core. After triggering an optimized exploit for the flaw, the researcher could leak sensitive data from any system operation, including those that take place in virtual machines, isolated sandboxes, containers, etc.

Ivanti released security patches for the remote unauthenticated API access vulnerability tracked as CVE-2023-35078 on Sunday. While Ivanti has published a security advisory to provide details on the security vulnerability, the information is being blocked by a login, given that the article can only be accessed with an account linked to Ivanti customer information.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products. With your permission we and our partners may use precise geolocation data and identification through device scanning.
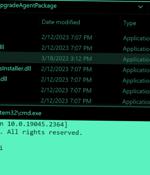
Zero-day vulnerabilities in Windows Installers for the Atera remote monitoring and management software could act as a springboard to launch privilege escalation attacks. "For instance, misconfigured Custom Actions running as NT AUTHORITYSYSTEM can be exploited by attackers to execute local privilege escalation attacks."
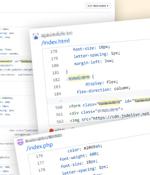
Cybersecurity researchers said they have discovered what they say is the first open-source software supply chain attacks specifically targeting the banking sector. "These attacks showcased advanced techniques, including targeting specific components in web assets of the victim bank by attaching malicious functionalities to it," Checkmarx said in a report published last week.

The Clop ransomware gang is copying an ALPHV ransomware gang extortion tactic by creating Internet-accessible websites dedicated to specific victims, making it easier to leak stolen data and further pressuring victims into paying a ransom. This stolen data is used as leverage in double-extortion attacks, warning victims that the data will be leaked if a ransom is not paid.

Thousands of Citrix Netscaler ADC and Gateway servers exposed online are likely vulnerable against a critical remote code execution bug exploited by unauthenticated attackers in the wild as a zero-day. "We tag all IPs where we see a version hash in a Citrix instance. This is due fact that Citrix has removed version hash information in recent revisions," Shadowserver said.

Thousands of Citrix Netscaler ADC and Gateway servers exposed online are likely vulnerable against a critical remote code execution bug exploited by unauthenticated attackers in the wild as a zero-day. "We tag all IPs where we see a version hash in a Citrix instance. This is due fact that Citrix has removed version hash information in recent revisions," Shadowserver said.

The chart shows that extortion attacks with the lowest complexity and automation have the least impact on victims and cost to the attackers. On May 27th, the Clop ransomware gang began widespread data-theft attacks exploiting a zero-day vulnerability in the MOVEit Transfer secure file transfer platform.