Security News

New research from Proofpoint exposes a new massive credential phishing attack campaign aimed at top-level executives in more than 100 organizations worldwide. This cybersecurity attack leverages the EvilProxy phishing kit and bypasses two-factor authentication.

"Our attacks are not computationally expensive, meaning anyone with the appropriate network access can perform them, and they are independent of the VPN protocol being used," claim Nian Xue of New York University; Yashaswi Malla, Zihang Xia, and Christina Pöpper of New York University Abu Dhabi; and Mathy Vanhoef of KU Leuven University. "Even if the victim is using another layer of encryption such as HTTPS, our attacks reveal which websites a user is visiting, which can be a significant privacy risk."
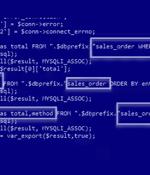
E-commerce sites using Adobe's Magento 2 software are the target of an ongoing campaign that has been active since at least January 2023. The attacks, dubbed Xurum by Akamai, leverage a now-patched critical security flaw in Adobe Commerce and Magento Open Source that, if successfully exploited, could lead to arbitrary code execution.

Germany's Federal Office for the Protection of the Constitution has warned of cyber attacks targeting Iranian persons and organizations in the country since the end of 2022. "The cyber attacks were mainly directed against dissident organizations and individuals - such as lawyers, journalists, or human rights activists - inside and outside Iran," the agency said in an advisory.

Entities using the name and iconography of Anonymous claim to have conducted cyberprotests against the Japanese government for actions related to the release of wastewater from the Fukushima Daini Nuclear Power Plant. In an operation dubbed "Tango Down", The Anonymous Italia Collective claims to have attacked 21 government and other websites associated with the decision to release wastewater from the Fukushima facility, which in 2011 infamously experienced damage to three reactor cores after an earthquake and tsunami disabled safety systems.

A team of researchers from UC Irvine and Tsinghua University has developed a new powerful cache poisoning attack named 'MaginotDNS,' that targets Conditional DNS resolvers and can compromise entire TLDs top-level domains. The concept of DNS cache poisoning is injecting forged answers into the DNS resolver cache, causing the server to direct users who enter a domain to incorrect IP addresses, potentially leading them to malicious websites without their knowledge.

A high-severity security flaw has been disclosed in the Python URL parsing function that could be exploited to bypass domain or protocol filtering methods implemented with a blocklist, ultimately resulting in arbitrary file reads and command execution. "Urlparse has a parsing problem when the entire URL starts with blank characters," the CERT Coordination Center said in a Friday advisory.

We share specifics from new security research about dependency confusion attacks, as well as explain how these attacks work, who is most at risk and how to mitigate them. New research from OX Security, a DevOps software supply chain security company, revealed that almost all applications with more than one billion users and more than 50% of applications with 30 million users are using dependencies that are vulnerable to dependency confusion attacks.

Ecommerce stores using Adobe's open source Magento 2 software are being targeted by an ongoing exploitation campaign based on a critical vulnerability that was patched last year, on February 13, 2022. "The attacker seems to be interested in payment stats from the orders in the victim's Magento store placed in the past 10 days," they said.

The U.S. government released a report after analyzing simple techniques, e.g. SIM swapping, used by the Lapsus$ extortion group to breach dozens of organizations with a strong security posture. The group used SIM swapping to gain access to a target company's internal network and steal confidential information like source code, details about proprietary technology, or business and customer-related documents.