Security News
The advanced persistent threat actor known as Winter Vivern is now targeting officials in Europe and the U.S. as part of an ongoing cyber espionage campaign. "TA473 since at least February 2023 has continuously leveraged an unpatched Zimbra vulnerability in publicly facing webmail portals that allows them to gain access to the email mailboxes of government entities in Europe," Proofpoint said in a new report.

An unknown Chinese state-sponsored hacking group has been linked to a novel piece of malware aimed at Linux servers. "The rootkit has a limited set of features, mainly installing a hook designed for hiding itself."

The advanced persistent threat known as Winter Vivern has been linked to campaigns targeting government officials in India, Lithuania, Slovakia, and the Vatican since 2021. The activity targeted Polish government agencies, the Ukraine Ministry of Foreign Affairs, the Italy Ministry of Foreign Affairs, and individuals within the Indian government, SentinelOne said in a report shared with The Hacker News.

Sentinel Labs has previously seen spreadsheet files with malicious macros that launch PowerShell being dropped on cloned sites used by the APT. Deploying fake virus scanners. One example of Winter Vivern's resourcefulness in the Sentinel Labs report is the use of Windows batch files to impersonate antivirus scanners while, in reality, downloading malicious payloads.
A cyberespionage actor known as Tick has been attributed with high confidence to a compromise of an East Asian data-loss prevention company that caters to government and military entities. "The attackers compromised the DLP company's internal update servers to deliver malware inside the software developer's network, and trojanized installers of legitimate tools used by the company, which eventually resulted in the execution of malware on the computers of the company's customers," ESET researcher Facundo Muñoz said.
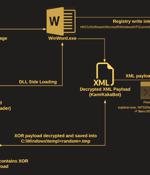
The Dark Pink advanced persistent threat actor has been linked to a fresh set of attacks targeting government and military entities in Southeast Asian countries with a malware called KamiKakaBot. Dark Pink, also called Saaiwc, was first profiled by Group-IB earlier this year, describing its use of custom tools such as TelePowerBot and KamiKakaBot to run arbitrary commands and exfiltrate sensitive information.

ESET researchers have analyzed MQsTTang, a custom backdoor that they attribute to the China-aligned Mustang Panda APT group. Due to the nature of the decoy filenames used, researchers believe that political and governmental organizations in Europe and Asia are also being targeted.
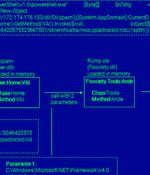
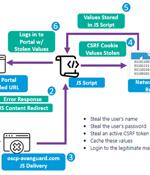
The threat actor known as Blind Eagle has been linked to a new campaign targeting various key industries in Colombia. Blind Eagle, also known as APT-C-36, was recently covered by Check Point Research, detailing the adversary's advanced toolset comprising Meterpreter payloads that are delivered via spear-phishing emails.

Government and military organizations in the Asia Pacific region are being targeted by a previously unknown advanced persistent threat actor, per the latest research. Singapore-headquartered Group-IB, in a report shared with The Hacker News, said it's tracking the ongoing campaign under the name Dark Pink and attributed seven successful attacks to the adversarial collective between June and December 2022.

Attacks targeting government agencies and military bodies in multiple countries in the APAC region have been attributed to what appears to be a new advanced threat actor that leverages custom malware to steal confidential information. Security researchers refer to this group as Dark Pink or Saaiwc Group, noting that it employs uncommon tactics, techniques, and procedures.