Security News

The China-linked advanced persistent threat (APT) group. known as Aquatic Panda has been linked to a "global espionage campaign" that took place in 2022 targeting seven organizations. These...

State-sponsored threat actors and cybercrime groups from North Korea, Iran, Russia, and China have been exploiting a zero-day Windows vulnerability with no fix in sight for the last eight years,...

Maritime and logistics companies in South and Southeast Asia, the Middle East, and Africa have become the target of an advanced persistent threat (APT) group dubbed SideWinder. The attacks,...

The threat actor known as Lotus Panda has been observed targeting government, manufacturing, telecommunications, and media sectors in the Philippines, Vietnam, Hong Kong, and Taiwan with updated...

A new campaign is targeting companies in Taiwan with malware known as Winos 4.0 as part of phishing emails masquerading as the country's National Taxation Bureau. The campaign, detected last month...

A subgroup of Russia’s Sandworm APT has been working to achieve initial and persistent access to the IT networks of organizations working in economic sectors Russia is interested in. “In 2022, its...

The North Korea-linked nation-state hacking group known as Kimsuky has been observed conducting spear-phishing attacks to deliver an information stealer malware named forceCopy, according to new...
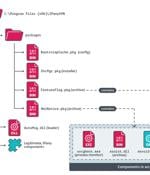
A previously undocumented China-aligned advanced persistent threat (APT) group named PlushDaemon has been linked to a supply chain attack targeting a South Korean virtual private network (VPN)...

ESET researchers have uncovered a supply chain attack targeting a South Korean VPN provider, carried out by PlushDaemon, a newly identified China-aligned APT group. In this cyberespionage...

The United States Treasury Department said it suffered a "major cybersecurity incident" that allowed suspected Chinese threat actors to remotely access some computers and unclassified documents. ...