Security News

Kaspersky's security researchers have uncovered a long-running spyware campaign targeting Android users that bears the marks of Vietnam-linked hacking group OceanLotus. Multiple variants of the malware were identified by BlackBerry researchers too, who included information on them in a report published in October 2019.
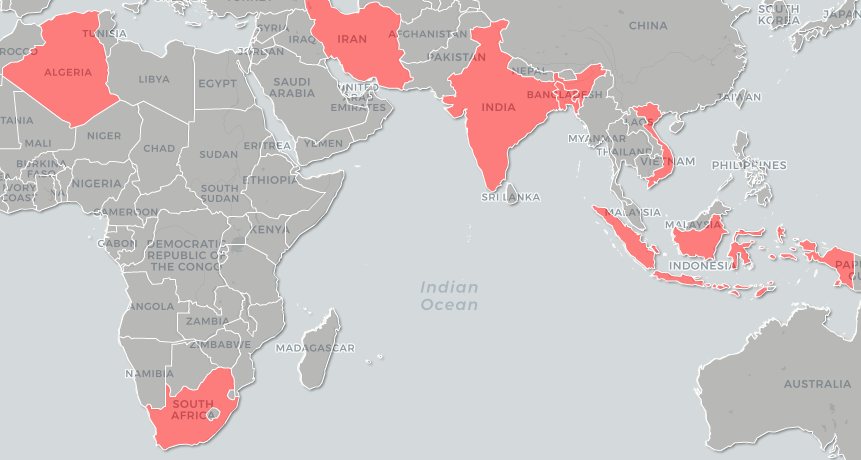
Dubbed PhantomLance by Kaspersky, the campaign is centered around a complex spyware that's distributed via dozens of apps within the Google Play official market, as well as other outlets like the third-party marketplace known as APKpure. Kaspersky's report follows previous research from BlackBerry, which connected OceanLotus to a trio of fake apps for Android last year.

The attack accuses victims of possessing pornography, encrypts all files on the device, and then instructs them to pay a fine to unlock the data, according to Check Point Research. After a successful infection on an Android device, Lucy encrypts files and then displays a ransom note in a browser window.

Rabobank's Australian outpost has messed up its Android app, leaving an unknown number of users unable to access their bank accounts on mobile devices. Customers brought The Register's attention to the pile of woeful reviews for the bank's app, many featuring a complaint that it produces the error "Unable to connect please check your internet connection".

"While our team has seen earlier versions of this trojan, which only featured a basic SMS stealer, new, and more elaborate, feature of the overlay malware capability - a tactic common to most Android banking malware." "Abusing the Accessibility service on the device, a relatively common way for Android malware apps to keep tabs on which app is running in the foreground, [Banker.BR] waits for a match with the goal of launching overlay screens at the right time and context to fool the user into tapping their credentials into the overlay," said researchers.

Or, you could make use of a feature, introduced in Android 9, called SMS Verification Code Autofill. To enable SMS Verification Code Autofill, you must first enable Autofill.

Starting with Android 9, you can make two-factor authentication even easier.

Purporting to offer help and info on COVID-19, the apps can let hackers take control of devices to access files, contacts, the calendar, and more, according to Check Point Research. As cyber criminals exploit the coronavirus with phishing emails, ransomware, and other attacks, so too are they concocting phony coronavirus-themed apps to infect mobile devices.

Security solutions provider Avast this week announced the launch of an Android version of its Avast Secure Browser. Previously available for Windows and macOS, the browser aims to provide users with increased security and privacy while navigating the Internet, shopping, or accessing their bank accounts on their Android devices.

Google has removed an Android VPN program from the Google Play store after researchers notified it of a critical vulnerability. VPNpro, a company that reviews and advises on VPN products, warned in February of a vulnerability in the product that could cause a man in the middle attack, enabling an intruder to insert themselves between the user and the VPN service.