Security News

Google has patched a vulnerability in its Android OS that could allow attackers to completely take over someone's device to install programs, steal or change data, or create new accounts with full privileges. The flaw was one of 39 vulnerabilities affecting Android OS builds that use older security profiles and are spread throughout various components of Android that the company fixed in its latest security patch, according to a security bulletin published Monday.

Google this week released the May 2020 security patches for the Android operating system, which address several critical vulnerabilities, including one affecting the System component. A total of 39 vulnerabilities were patched with the release, split into two parts: 15 received fixes as part of the 2020-05-01 security patch level, and 24 addressed with the 2020-05-05 security patch level.

A threat actor managed to compromise more than 75% of the devices within a company by distributing their malware through a mobile device management server, Check Point reports. As part of the attack, cybercriminals were distributing a new variant of the Cerberus Android malware that was designed to collect large amounts of sensitive data and exfiltrate it to a remote command and control server.

A newly discovered piece of Android malware is targeting the users of close to 300 financial applications across the United States and Europe, Cybereason Nocturnus security researchers warn. Dubbed EventBot, the threat appears to be newly developed, as its code differs significantly from that of other Android malware out there.

Researchers have analysed a new strain of Android malware that does not yet exist in the wild. EventBot asks the user for permission to use accessibility services, a powerful feature since these services require extensive permissions in order to work, including acting as a keylogger, for example, and running in the background.
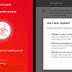
A new type of mobile banking malware has been discovered abusing Android's accessibility features to exfiltrate sensitive data from financial applications, read user SMS messages, and hijack SMS-based two-factor authentication codes. Called "EventBot" by Cybereason researchers, the malware is capable of targeting over 200 different financial apps, including banking, money transfer services, and crypto-currency wallets such as Paypal Business, Revolut, Barclays, CapitalOne, HSBC, Santander, TransferWise, and Coinbase.

A new type of mobile banking malware has been discovered abusing Android's accessibility features to exfiltrate sensitive data from financial applications, read user SMS messages, and hijack SMS-based two-factor authentication codes. Called "EventBot" by Cybereason researchers, the malware is capable of targeting over 200 different financial apps, including banking, money transfer services, and crypto-currency wallets such as Paypal Business, Revolut, Barclays, CapitalOne, HSBC, Santander, TransferWise, and Coinbase.

An Android mobile malware has been uncovered that steals payment data from users of popular financial apps like PayPal, Barclays, CapitalOne and more. EventBot is not currently on the Google Play app marketplace, but researchers said the malware is nonetheless masquerading as legitimate applications.

A piece of Android ransomware uses a scareware tactic to extort money from victims: it asks them to provide their credit card information to pay a "Fine," Check Point reveals. Dubbed Black Rose Lucy, or simply Lucy, the malicious program was initially discovered in 2018 as a Malware-as-a-Service botnet and dropper for Android devices.

The Android ecosystem continues to become more fragmented: several Android versions are supported at the same time, and unsupported end-of-life versions continue to be widely used. Only 30% of the observed devices were running Android 9 or newer in 2019, 40% were running Android 8, and 30% were running Android 7.