Security News

Specops Password Auditor is a read-only tool that scans your Active Directory and identifies password-related vulnerabilities. The collected information generates multiple interactive reports containing user and password policy information.

Microsoft is urging customers to patch two security vulnerabilities in Active Directory domain controllers that it addressed in November following the availability of a proof-of-concept tool on December 12. The two vulnerabilities - tracked as CVE-2021-42278 and CVE-2021-42287 - have a severity rating of 7.5 out of a maximum of 10 and concern a privilege escalation flaw affecting the Active Directory Domain Services component.

A proof-of-concept tool has been published that leverages two Windows Active Directory bugs fixed last month that, when chained, can allow easy Windows domain takeover. Both vulnerabilities are described as a "Windows Active Directory domain service privilege-escalation" bugs and are of high severity, with a CVSS criticality score of 7.5 out of 10.

Microsoft warned customers today to patch two Active Directory domain service privilege escalation security flaws that, when combined, allow attackers to easily takeover Windows domains.Redmond's warning to immediately patch the two bugs - both allowing attackers to impersonate domain controllers - comes after a proof-of-concept tool that can leverage these vulnerabilities was shared on Twitter and GitHub on December 11.

Microsoft Active Directory and Azure Active Directory are directory services products used for identity and access management at most major enterprises all over the world. All Active Directory environments are vulnerable to a type of attack called identity attack paths.

Researchers from the Microsoft Threat Intelligence Center have observed the APT it calls Nobelium using a post-exploitation backdoor dubbed FoggyWeb, to attack Active Directory Federation Services servers. Once a server is compromised, the threat group deploys FoggyWeb "To remotely exfiltrate the configuration database of compromised AD FS servers, decrypted token-signing certificates and token-decryption certificates," he said, which can be used to penetrate into users' cloud accounts.

Microsoft has warned of a new tool designed to exfiltrate credentials and introduce a backdoor into Active Directory servers that is under active use by the Nobelium threat actor group. The FoggyWeb malware, Microsoft has declared, is designed to target Microsoft Active Directory Federation Services servers, exfiltrating credentials, configuration databases, decrypted token-signing and token-decryption certificates, and to download additional components to set up a permanent backdoor and attack the network more widely.
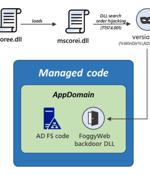
Microsoft on Monday revealed new malware deployed by the hacking group behind the SolarWinds supply chain attack last December to deliver additional payloads and steal sensitive information from Active Directory Federation Services servers. "Once Nobelium obtains credentials and successfully compromises a server, the actor relies on that access to maintain persistence and deepen its infiltration using sophisticated malware and tools," MSTIC researchers said.

Jack Wallen walks you through the steps to join Ubuntu Desktop to Active Directory domains.

My guests today are Lee Christiansen and Will Schroeder, the SpecterOps researchers behind a recent report entitled Certified Pre-owned: Abusing Active Directory Certificate Servers, about attack paths in Microsoft Active Directory. Will Schroeder: And the last thing I'll add on to that last kind of point is just the complexity of Active Directory along with, you know, how easy it can occasionally be to where one of the things we've seen and a term we've tried to help kind of push is misconfiguration debt, where we see Active Directory has been in an environment for a long period of time.