Security News > 2024

A security flaw has been disclosed in Kyocera’s Device Manager product that could be exploited by bad actors to carry out malicious activities on affected systems. "This vulnerability allows...
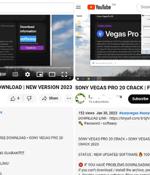
Threat actors are resorting to YouTube videos featuring content related to cracked software in order to entice users into downloading an information stealer malware called Lumma. “These YouTube...

The year 2023 marks a significant milestone for Windows 11 with the introduction of several new features and improvements. Windows 11 introduces Windows Copilot, an innovative AI assistant that merges the capabilities of Bing Chat with additional plugins.

Why is it that when a company becomes aware of a potential data security incident, the team working on it have an immediate and overwhelming feeling that the company is doomed? And yet, when there's another kind of high-risk event, such as an ethics investigation, it doesn't cause the same apocalyptic feelings? Cybersecurity professionals in legal and IT security departments have key roles in working through a data security incident, but often fail to build up a trusted relationship in advance.

In this Help Net Security interview, Phil Vachon, Head of Infrastructure in the Office of the CTO at Bloomberg, discusses the varying definitions of zero trust among security professionals and companies, emphasizing its broad design philosophy. Why does the definition of zero trust vary so significantly among security professionals and companies? How do these variations impact companies' approach toward implementing zero trust?

As AI tools become more widespread, impersonation and deception have become easier. Organizations are combating this issue with policies and technological solutions.

The publication, "Adversarial Machine Learning: A Taxonomy and Terminology of Attacks and Mitigations," is a key component of NIST's broader initiative to foster the creation of reliable AI. This effort aims to facilitate the implementation of NIST's AI Risk Management Framework and aims to assist AI developers and users in understanding potential attacks and strategies to counter them, acknowledging that there is no silver bullet. "The risks of AI are as significant as the potential benefits. The latest publication from NIST is a great start to explore and categorize attacks against AI systems. It defines a formal taxonomy and provides a good set of attack classes. It does miss a few areas, such as misuse of the tools to cause harm, abuse of inherited trust by people believing AI is an authority, and the ability to de-identify people and derive sensitive data through aggregated analysis," Matthew Rosenquist, CISO at Eclipz.io commented.

Think you're too small to experience a cyber attack? That's not the case. Cyber threat actors are increasingly setting their sights on small businesses.

Toronto Zoo, the largest zoo in Canada, says that a ransomware attack that hit its systems on early Friday had no impact on the animals, its website, or its day-to-day operations. "Currently, our animal wellbeing, care and support systems have not been impacted by this incident and we are continuing with normal Zoo operations including being open to guests," it said.

The official Netgear and Hyundai MEA Twitter/X accounts are the latest hijacked to push scams designed to infect potential victims with cryptocurrency wallet drainer malware. Hackers are increasingly targeting and compromising verified government and business X accounts with 'gold' and 'grey' checkmarks to add legitimacy to their malicious tweets pushing cryptocurrency scams, phishing sites, and sites dropping crypto drainers.