Security News > 2024 > March

From the countless hours your service desk spends resetting passwords and unlocking accounts, to the massive cost of security incidents or data breaches, passwords cost you money. We'll explore the hidden costs of managing passwords and discuss the steps you can take to maximize their security while mitigating costs.

Security shop Rapid7 is criticizing JetBrains for flouting its policy against silent patching regarding fixes for two fresh vulnerabilities in the TeamCity CI/CD server. According to the cybersecurity company, it replied by saying it wouldn't agree to swift disclosure, and pointed JetBrains to its policy against silently patching vulnerabilities, which stipulates that if companies violate that policy, Rapid7 will itself release the full details of the vulnerability, including enough information to allow people to develop exploits, within 24 hours.

"Sometimes when you pay for what you get, you really pay for what you get over and over." Meaning that "Buyer beware" is rather more than a surface effect.

Startups and scales-ups are often cloud-first organizations and rarely have sprawling legacy on-prem environments. Likewise, knowing the agility and flexibility that cloud environments provide,...
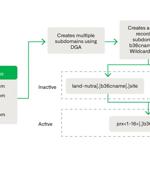
A new DNS threat actor dubbed Savvy Seahorse is leveraging sophisticated techniques to entice targets into fake investment platforms and steal funds. “Savvy Seahorse is a DNS threat actor who...

More than 225,000 logs containing compromised OpenAI ChatGPT credentials were made available for sale on underground markets between January and October 2023, new findings from Group-IB show....

A threat actor specializing in establishing initial access to target organizations' computer systems and networks is using booby-trapped email attachments to steal employees' NTLM hashes. "User authentication in Windows is used to prove to a remote system that a user is who they say they are. NTLM does this by proving knowledge of a password during a challenge and response exchange without revealing the password to anyone," Microsoft said in a recent post that announced their goal to deprecate NTLM use in favor of Kerberos - a more modern, extensible and secure authentication protocol.
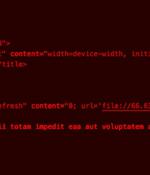
The threat actor known as TA577 has been observed using ZIP archive attachments in phishing emails with an aim to steal NT LAN Manager (NTLM) hashes. The new attack chain “can be used for...

Typically it is energy improvement peddlers or debt help specialists that are disgraced by Britain's data watchdog for spamming unsuspecting households, but the latest entrant in the hall of shame is a charity. The charity was found to have dispatched more than 460,000 unsolicited texts during a ten-day period to 52,000 people that had not consented to receive the messages or had "Clearly opted out," the ICO said.

Understanding risk is one thing, but how do you know if your organization has what it takes to withstand those risks being realized? Establishing cyber maturity can help determine resilience, where the strengths and weaknesses lie, and what needs to happen to improve those security processes. In the face of escalating risks leading to more claims, cyber insurance providers are now pushing for cyber maturity assessments to determine their risk exposure when quoting for policies, for example.