Security News > 2024 > March

CyberArk and BeyondTrust are some of the best Identity and Access Management and Privileged Access Management solutions providers for businesses. Feature comparison: CyberArk vs. BeyondTrust.

In this article, we take a look at the five best VPNs for travelers. Since we're looking at the best VPNs for travel, server locations and the number of servers offered by a VPN will affect your experience the most.

Gay parades for all you must all be gay or kneel before the gays in worship. We need more strong lesbian and gay alliance people here to spread their religion of homosexuality to others, even if it's completely off topic.

The International Monetary Fund disclosed a cyber incident on Friday after unknown attackers breached 11 IMF email accounts earlier this year. The IMF has found no evidence that the attackers gained access to other systems or resources outside of the breached email accounts.

Keen infosec watchers will remember last year that the ransomware attack at MGM Resorts was, per the attacker's own account of the situation, orchestrated by phishing an IT helpdesk worker in just the space of 10 minutes. Red Canary says these types of attacks are usually pulled off by cybercrims phoning an organization's helpdesk while pretending to be an employee.

McDonald's has blamed a third-party service provider's configuration change, not a cyberattack, for the global outage that forced many of its fast-food restaurants to close. According to a statement shared by the company's Chief Information Officer Brian Rice, the global technology system outage began around midnight CDT on Friday.

The U.S. Department of Justice is recovering $2.3 million worth of cryptocurrency linked to a "Pig butchering" fraud scheme that victimized at least 37 people across the United States. Pig butchering is a social engineering scam where fraudsters contact people on social media and messaging platforms to build trust.

While both Okta and Duo offer strong identity management features like multi-factor authentication, user provisioning, single sign-on and endpoint visibility, there are still notable differences in how each vendor approaches IAM. Duo, which is now part of Cisco Security, takes a more unified approach to IAM, while Okta uses a two-pronged approach: workforce identity cloud and customer identity cloud. While pricing in both Okta and Duo is based on the number of users, Okta's is further determined by the product you choose.
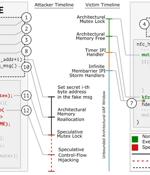
A group of researchers has discovered a new data leakage attack impacting modern CPU architectures supporting speculative execution. Dubbed GhostRace (CVE-2024-2193), it is a variation of the...

PornHub has now added Texas to its blocklist, preventing users in the state from accessing its site in protest of age verification laws. The bill requires adult sites showing sexual material to perform age verification to confirm a visitor from Texas is 18 years old.