Security News > 2024 > February

Japan's Computer Security Incident Response Team is warning that the notorious North Korean hacking group Lazarus has uploaded four malicious PyPI packages to infect developers with malware. PyPI is a repository of open-source software packages that software developers can utilize in their Python projects to add additional functionality to their programs with minimal effort.

This article takes a look at some lessons from recent phishing attacks and highlights actionable tips to limit the risks of phishing affecting your company. In the face of rampant phishing attacks that can cause large-scale data breaches, here are some ways you can limit phishing risks.

Pepco Group has confirmed that its Hungarian business has been hit by a "Sophisticated fraudulent phishing attack." The European company, which operates shops under the Pepco, Poundland and Dealz brands, said that the company lost approximately €15.5 million in cash as a consequence of the attack.

A threat actor named Savvy Seahorse is abusing CNAME DNS records Domain Name System to create a traffic distribution system that powers financial scam campaigns. Using DNS CNAME records as a TDS. Savvy Seahorse creatively uses Canonical Name records as a Traffic Distribution System for its operations, allowing threat actors to easily manage changes, such as performing IP rotation that enhances detection evasion.
The U.S. government is warning about the resurgence of BlackCat (aka ALPHV) ransomware attacks targeting the healthcare sector as recently as this month. "Since mid-December 2023, of the nearly 70...

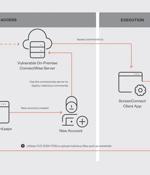
Suspected Chinese state-sponsored hackers leveraging Ivanti Connect Secure VPN flaws to breach a variety of organizations have demonstrated "a nuanced understanding of the appliance", according to Mandiant incident responders and threat hunters. "While the limited attempts observed to maintain persistence have not been successful to date due to a lack of logic in the malware's code to account for an encryption key mismatch, it further demonstrates the lengths UNC5325 will go to maintain access to priority targets and highlights the importance of ensuring network appliances have the latest updates and patches," Mandiant's specialists noted.

One possible solution, touted by former Department of Homeland Security Secretary Michael Chertoff on a recent podcast, would be for the federal government to step in and help pay for these sorts of attacks by providing a cyber insurance backstop. A cyber insurance backstop would provide a means for insurers to receive financial support from the federal government in the event that there was a catastrophic cyberattack that caused so much financial damage that the insurers could not afford to cover all of it.

In today's digital era, data privacy isn't just a concern; it's a consumer demand. Businesses are grappling with the dual challenge of leveraging customer data for personalized experiences while...

Registrars can now block people from registering tens of thousands of domain names that look like, are spelling variations of, or otherwise infringe on brand names. While the basic plan lets subscribers block specific domain names that read like their trademark across some 563 extensions, the "Plus" version takes a huge leap forward.

Superusers Need Super Protection: How to Bridge Privileged Access Management and Identity Management
Traditional perimeter-based security has become costly and ineffective. As a result, communications security between people, systems, and networks is more important than blocking access with...