Security News > 2024 > February
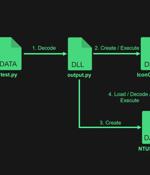
The notorious North Korean state-backed hacking group Lazarus uploaded four packages to the Python Package Index (PyPI) repository with the goal of infecting developer systems with malware. The...

BobTheSmuggler is an open-source tool designed to easily compress, encrypt, and securely transport your payload. It basically enables you to hide a payload in plain sight. "In many of my red team engagements, I encountered scenarios where I had to deliver a payload to the target, and due to a DLP or firewall rule, the payload delivery was blocked. I quickly opted for the HTML smuggling technique for payload delivery, but none of the publicly available tools had the feature to hide the payload inside PNG/GIF. Most tools would just base64 encode the binary and embed it inside the HTML file. Due to this reason, the HTML file size would increase to a few MBs. This file wouldn't be ideal for sending as an email attachment due to size constraints, Harpreet Singh, the creator of BobTheSmuggler, told Help Net Security."
At least two different suspected China-linked cyber espionage clusters, tracked as UNC5325 and UNC3886, have been attributed to the exploitation of security flaws in Ivanti Connect Secure VPN...

What are the most pressing identity security risks and threats for organizations in 2024? To address these complexities, organizations need business users and security teams to collaborate on an identity management and governance framework and overarching processes for policy-based authentication, SSO, lifecycle management, security and compliance.

U.S. President Joe Biden has issued an Executive Order that prohibits the mass transfer of citizens' personal data to countries of concern. The Executive Order also "provides safeguards around...

In 2004, Android was two people who wanted to build camera software but couldn't get investors interested. Roid is a large team at Google today, delivering an OS to over 3 billion devices worldwide.

Chinese PC maker Acemagic has admitted some of its products shipped with pre-installed malware. YouTuber The Net Guy found malware on Acemagic mini PCs when he tested them in early February.

As commercial adoption of cloud technologies continues, cloud-focused malware campaigns have increased in sophistication and number - a collective effort to safeguard both large and small enterprises is critical, according to Cado Security. Although cloud-focused attackers aim to exploit various services typically deployed in cloud environments, Docker remains the most frequently targeted for initial access, with 90.65% of honeypot traffic when discounting SSH. Identified malware campaigns, such as P2Pinfect, had a wide geographical distribution with nodes belonging to providers in China, the US, and Germany, which shows that regardless of where your infrastructure is located, it is still susceptible to Linux and cloud-focused attacks.

76% of enterprises lack sufficient voice and messaging fraud protection as AI-powered vishing and smishing skyrocket following the launch of ChatGPT, according to Enea. 61% of enterprises still suffer significant losses to mobile fraud, with smishing and vishing being the most prevalent and costly.

Please turn on your JavaScript for this page to function normally. SaaS sprawl introduces security risks, operational headaches, and eye-popping subscription costs.