Security News > 2023

Taiwan-based NAS maker Synology has addressed a maximum severity vulnerability affecting routers configured to run as VPN servers. VPN Plus Server is a virtual private network server that allows administrators to set up Synology routers as a VPN server to allow remote access to resources behind the router.

An enforcement-based approach to security begins with a security policy backed by security controls, often heavy-handed and designed to prevent employees from engaging in risky behavior or inadvertently expanding the potential attack surface of an organization. Most organizations exclusively use enforcement-based security controls, usually carried out at the network level with a Cloud Access Security Broker or a Security Services Edge.
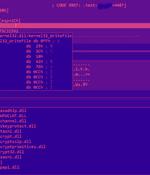
A new malware campaign has been observed using sensitive information stolen from a bank as a lure in phishing emails to drop a remote access trojan called BitRAT. The unknown adversary is believed to have hijacked the IT infrastructure of a Colombian cooperative bank, using the information to craft convincing decoy messages to lure victims into opening suspicious Excel attachments. The leaked details include Cédula numbers, email addresses, phone numbers, customer names, payment records, salary details, and addresses, among others.

Financial and insurance sectors in Europe have been targeted by the Raspberry Robin worm, as the malware continues to evolve its post-exploitation capabilities while remaining under the radar. "What is unique about the malware is that it is heavily obfuscated and highly complex to statically disassemble," Security Joes said in a new report published Monday.

The answer the second question - How to make Kali the best possible platform for training? - we work very closely with the OffSec content development team to find out what tools they are using for training, what sort of default environment works best for learners, and what we can do in Kali to support general education efforts. Surprisingly, even though Kali is built for advanced information security work, it is often the first Linux many users ever use.

The cybersecurity industry will undergo some significant changes in 2023. As more systems get connected, we can expect to see more outages.
Raj Samani, SVP, Chief Scientist, Rapid7, discusses the tactics observed from a recent case of espionage, and what can be learned from such observations. This video was recorded at IRISSCON 2022, an annual conference organized by IRISSCERT. The all-day event focuses on providing attendees with an overview of the current cyber threats facing businesses in Ireland and what they can do to help deal with those threats.

78% of security professionals expect breach and incident reporting requirements to create more work for their teams, and 77% expect increased work from privacy requirements. "Regulatory developments around both incident reporting and privacy will undoubtedly continue to ramp up in 2023," said Bill Bernard, AVP, Security Strategy at Deepwatch.

Ransomware attacks in 2022 impacted more than 200 hundred larger organizations in the U.S. public sector in the government, educational, and healthcare verticals. [...]
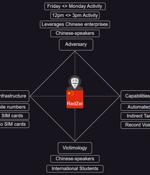
Chinese international students in the U.K. have been targeted by persistent Chinese-speaking scammers for over a year as part of an activity dubbed RedZei. The most notable aspect about the operation is the steps taken by the threat actors to bypass steps taken by users to prevent scam calls, using a new pay-as-you-go U.K. phone number for each wave so as to render phone number-based blocking ineffective.