Security News > 2023

In an increasingly digital world, no organization is spared from cyber threats. Yet, not every organization has the luxury of hiring a full-time, in-house CISO. This gap in cybersecurity...
Cybersecurity researchers have discovered 18 malicious loan apps for Android on the Google Play Store that have been collectively downloaded over 12 million times. "Despite their attractive...

In the ever-evolving cybersecurity landscape, one method stands out for its chilling effectiveness – social engineering. But why does it work so well? The answer lies in the intricate dance...

Co-founder Roman Khavronenko, who was speaking to us at a recent Kubecon event about open source, licensing, and the pressure of accepting venture capital, opines that, barring a few success stories, "In most cases, startups fail because of this huge pressure." The company operates open source time series database monitoring.

With its innovative feature for generating reliable Vulnerability Exploitability eXchange documents, Kubescape became the first open-source project to provide this functionality. Vulnerability Exploitability eXchange is a standard that facilitates the sharing and analyzing of information about vulnerabilities and their potential for exploitation.

The survey results clearly indicate that many IT professionals are not familiar with or don't see the value of certificate automation. Given the cost of certificate outages, this will be a precarious situation for IT professionals and security teams if they don't have a solid plan to deal with the accelerated certificate lifecycle management.
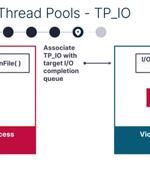
A new collection of eight process injection techniques, collectively dubbed PoolParty, could be exploited to achieve code execution in Windows systems while evading endpoint detection and response...

Enhancing its predecessor, the SCS 9001 2.0 standard presents a more comprehensive global cybersecurity and supply chain security framework adaptable to various communication networks across industries and sectors. How does the SCS 9001 2.0 standard differ from its predecessor regarding cybersecurity and supply chain security?

Cybercriminals still prefer targeting open remote access products, or like to leverage legitimate remote access tools to hide their malicious actions, according to WatchGuard. "Threat actors continue using different tools and methods in their attack campaigns, making it critical for organizations to keep abreast of the latest tactics to fortify their security strategy," said Corey Nachreiner, chief security officer at WatchGuard.

The use of automated security technology is growing rapidly, which in turn is propagating the "Shift everywhere" philosophy - performing security tests throughout the entire software development life cycle - across more organizations, according to Synopsys. This year's findings revealed a clear trend of firms increasingly taking advantage of security automation to replace manual, subject matter expert-driven security activities to reduce cost and improve effectiveness.