Security News > 2023 > May

A recently patched vulnerability in Oracle Opera, a property management system widely used in large hotel and resort chains, is more critical than Oracle says it is and could be easily exploited by unauthenticated remote attackers to access sensitive information, a group of researchers has warned. Oracle Opera, also known as Micros Opera, is a solution many companies in the hospitality industry - more specifically, those offering lodging and related services - use to manage reservations, sales, housekeeping, catering, and deliver personalized guest experiences.

There has been a noted increase in malvertising via Google Ads this year, aimed at tricking users into downloading malware; among these malicious payloads is LOBSHOT, an infostealer that can also establish and keep long-term remote control of target computers through a hVNC module. LOBSHOT, an infostealer and remote access trojan, is being distributed via Google Ads.

A new Android surveillanceware possibly used by the Iranian government has been used to spy on over 300 individuals belonging to minority groups. "The spyware may also have been used in efforts to counter and monitor illegal trafficking activity related to arms, drugs, and alcohol," Lookout said, based on exfiltrated data that contained photos of drugs, firearms, and official documents issued by FARAJA. BouldSpy, like other Android malware families, abuses its access to Android's accessibility services and other intrusive permissions to harvest sensitive data such as web browser history, photos, contact lists, SMS logs, keystrokes, screenshots, clipboard content, microphone audio, and video call recordings.

These changes, coupled with the need for stronger collaboration with third-party vendors, have led them to SaaS applications to handle their CRM. Today, telecoms are using SaaS apps for billing, HR, call management, field operations management, tracking call center effectiveness, and hundreds of other applications. The advertisers are given access to the telecom's SaaS apps, where they can mine for data and develop powerful marketing and advertising campaigns.

The security updating of iPhones, iPads and Macs has entered a new stage: Apple has, for the first time, released a Rapid Security Response to owners of the devices running the latest versions of its operating systems. Announced nearly a year ago, the security-focused feature makes user devices automatically install security patches as they are made available.

Data loss - particularly from ransomware attacks - has always been a costly proposition for enterprises. In its 2023 Data Security Incident Response Report [PDF], Cleveland-based law firm BakerHostetler - which three years ago launched a practice around data, equal to other practices like tax, IP, and litigation - found while the number of ransomware incidents the firm responded to dipped in early 2022, it came roaring back toward the end of the year and into early 2023.

Researchers are warning about an infostealer mimicking a ChatGPT Windows desktop client that's capable of copying saved credentials from the Google Chrome login data folder. ChatGPT has not released an official desktop client, but this bogus version looks remarkably similar to what one would expect.
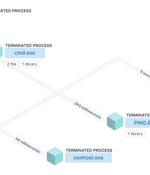
In yet another instance of how threat actors are abusing Google Ads to serve malware, a threat actor has been observed leveraging the technique to deliver a new Windows-based financial trojan and information stealer called LOBSHOT. "LOBSHOT continues to collect victims while staying under the radar," Elastic Security Labs researcher Daniel Stepanic said in an analysis published last week. The American-Dutch company attributed the malware strain to a threat actor known as TA505 based on infrastructure historically connected to the group.
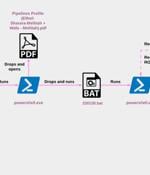
The North Korean threat actor known as ScarCruft began experimenting with oversized LNK files as a delivery route for RokRAT malware as early as July 2022, the same month Microsoft began blocking macros across Office documents by default. Other bespoke malware used by the group include, but not limited to, Chinotto, BLUELIGHT, GOLDBACKDOOR, Dolphin, and, most recently, M2RAT. It's also known to use commodity malware such as Amadey, a downloader that can receive commands from the attacker to download additional malware, in a bid to confuse attribution.
The Kremlin-backed threat group APT28 is flooding Ukrainian government agencies with email messages about bogus Windows updates in the hope of dropping malware that will exfiltrate system data. Executing the command simulates a Windows update but actually downloads and executes a PowerShell script that collects basic system information about using such commands as "Tasklist" and "Systeminfo".